Assign Permissions to the App Service
The EntraID SCIM microservice requires specific permissions to interact with Microsoft Graph API and Azure resources. You can implement permissions using two approaches: tenant-wide application permissions for simplicity, or custom Azure roles with least privilege for enhanced security. Choose the approach that best aligns with your organization's security policies and compliance requirements.
Permission Assignment Approaches
Approach 1: Tenant-Wide Application Permissions (Traditional)
This approach provides broad access across your entire EntraID tenant with simple management through single permission assignments. Ideal for:
- Standard deployments where broad access is acceptable
- Organizations without strict least-privilege requirements
- Development and testing environments requiring quick setup
- Simplified permission management with one-time admin consent for all permissions
- Faster initial configuration with minimal administrative overhead
Approach 2: Entra ID (Azure AD) Custom Role with Least Privilege (Recommended)
This approach offers granular control with permissions scoped to specific resources, providing enhanced security with minimal blast radius if credentials are compromised. Best suited for:
- Enterprise environments with strict security policies
- Compliance requirements mandating minimal access (meets most regulatory frameworks)
- Multi-tenant or shared environments requiring precise access control
- Organizations following Zero Trust principles
- Flexible scoping where permissions can be limited to specific groups, OUs, or resources
- Advanced security needs requiring detailed audit trails and permission lifecycle management
Implementation Guide
Approach 1: Tenant-Wide Application Permissions
This approach grants broad permissions across your entire EntraID tenant. The managed identity will have access to all resources of the specified types.
Required Microsoft Graph API Permissions
Core Permissions (Required for all deployments):
$CorePermissions = @(
"Directory.Read.All",
"Organization.Read.All",
"User.Read.All",
"User.ReadWrite.All",
"Group.Read.All",
"Group.ReadWrite.All",
"GroupMember.Read.All",
"GroupMember.ReadWrite.All",
"Reports.Read.All",
"AuditLog.Read.All"
)
Extended Permissions (Based on features needed):
$ExtendedPermissions = @(
# Application Management
"Application.Read.All",
"Application.ReadWrite.All",
"AppRoleAssignment.ReadWrite.All",
# Role Management
"RoleManagement.Read.All",
"RoleManagement.ReadWrite.Directory",
# Security & Conditional Access
"Policy.Read.All",
"Policy.ReadWrite.ConditionalAccess",
"CustomSecAttributeDefinition.ReadWrite.All",
"CustomSecAttributeAssignment.ReadWrite.All",
# Authentication Methods
"UserAuthenticationMethod.ReadWrite.All",
# Domain Management
"Domain.Read.All"
)
PowerShell Script for Tenant-Wide Permissions
# Configuration
$webApp = "<Your-App-Service-Name>"
$subscriptionName = "<Your-Subscription-Name>"
$tenantID = "<Your-Tenant-ID>"
# Set tenant and subscription context
az login --tenant $tenantID
az account set -s $subscriptionName
# Get managed identity details
$principalId = $(az resource list -n $webApp --query [*].identity.principalId --out tsv)
$graphResourceId = $(az ad sp list --display-name "Microsoft Graph" --query [0].id --out tsv)
# Define permissions based on your requirements
$RequiredPermissions = @(
"Directory.Read.All",
"Organization.Read.All",
"User.Read.All",
"User.ReadWrite.All",
"Group.Read.All",
"Group.ReadWrite.All",
"GroupMember.Read.All",
"Reports.Read.All",
"AuditLog.Read.All",
"Application.Read.All",
"Policy.Read.All",
"RoleManagement.Read.All",
"Domain.Read.All"
)
# Apply permissions
$uri = "https://graph.microsoft.com/v1.0/servicePrincipals/$principalId/appRoleAssignments"
$RequiredPermissions | ForEach-Object {
$appRoleId = $(az ad sp list --display-name "Microsoft Graph" --query "[0].appRoles[?value=='$($_)' && contains(allowedMemberTypes, 'Application')].id" --output tsv)
$body = "{'principalId':'$principalId','resourceId':'$graphResourceId','appRoleId':'$appRoleId'}"
Write-Host "Assigning permission: $_"
az rest --method post --uri $uri --body $body --headers "Content-Type=application/json"
}
Write-Host "Tenant-wide permissions assigned successfully"
Verify Tenant-Wide Permissions
Method 1: PowerShell Verification
# Verify assigned permissions
$principalId = "<Your-Managed-Identity-Principal-ID>"
$uri = "https://graph.microsoft.com/v1.0/servicePrincipals/$principalId/appRoleAssignments"
$assignments = az rest --method get --uri $uri | ConvertFrom-Json
$assignments.value | Select-Object -Property resourceDisplayName, @{Name="Permission";Expression={$_.appRoleId}}
Method 2: Azure Portal Verification
You can also verify the permissions through the Azure portal:
- Navigate to Azure Active Directory → Enterprise Applications
- Filter by Application type: Select Managed Identities
- Find your App Service managed identity in the list
- Click on the managed identity name to open its details
- Go to Permissions in the left navigation menu
- Review the Microsoft Graph permissions that have been assigned
You should see all the permissions you assigned in the script with Admin consent granted, as shown below:
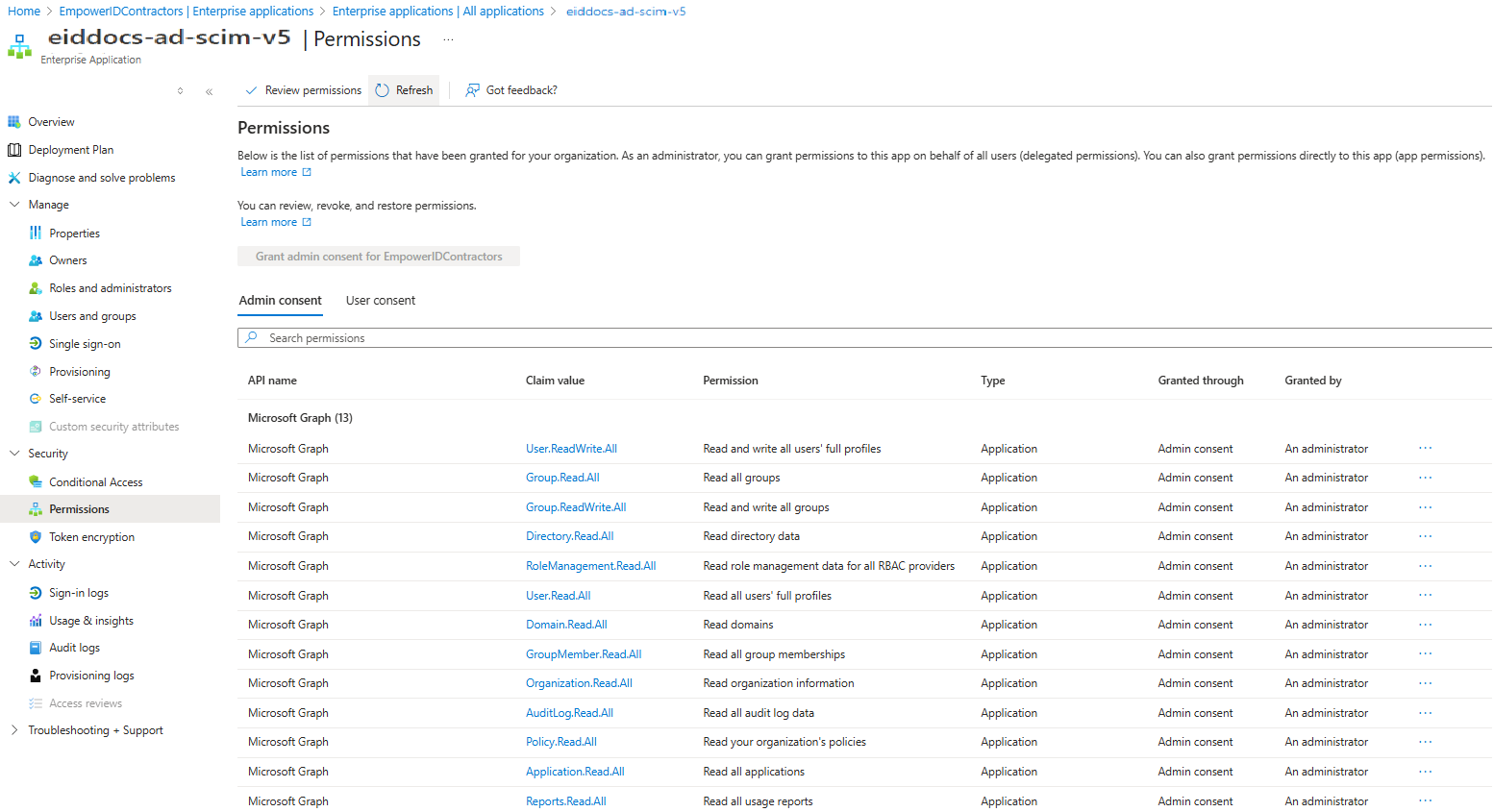
Approach 2: Entra ID (Azure AD) Custom Role with Least Privilege
This approach involves creating custom directory roles in Entra ID (formerly Azure AD) with the least required permissions and assigning them to your managed identity at the directory level. These roles enable granular access control over identity-related objects such as users, groups, applications, service principals, and licenses. They use the microsoft.directory/* permission set and are primarily intended for managing directory resources through the Microsoft Graph API.
Step 1: Create Entra ID (Azure AD) Custom Role with Limited Permissions
Create a custom directory role that only has permissions for User object read and update operations:
Connect-MgGraph -Scopes "RoleManagement.ReadWrite.Directory"
# Basic role information
$displayName = "EID SCIM Connector - Limited User Management"
$description = "Custom directory role for EmpowerID SCIM connector with limited user read and update permissions"
$templateId = (New-Guid).Guid
# Set of permissions to grant
$allowedResourceAction = @(
"microsoft.directory/users/appRoleAssignments/read",
"microsoft.directory/users/assignLicense",
"microsoft.directory/users/basic/update",
"microsoft.directory/users/contactInfo/update",
"microsoft.directory/users/directReports/read",
"microsoft.directory/users/extensionProperties/update",
"microsoft.directory/users/identities/read",
"microsoft.directory/users/jobInfo/update",
"microsoft.directory/users/licenseDetails/read",
"microsoft.directory/users/manager/read",
"microsoft.directory/users/manager/update",
"microsoft.directory/users/memberOf/read",
"microsoft.directory/users/passwordPolicies/update",
"microsoft.directory/users/scopedRoleMemberOf/read",
"microsoft.directory/users/standard/read",
"microsoft.directory/users/usageLocation/update"
)
$rolePermission = @{'allowedResourceActions'= $allowedResourceAction}
$rolePermissions = $rolePermission
# Create new custom admin role
$customRole = New-MgRoleManagementDirectoryRoleDefinition -Description $description `
-DisplayName $displayName -RolePermissions $rolePermissions -TemplateId $templateId -IsEnabled
Step 2: Assign Custom Directory Role to Managed Identity at Directory Scope
Assign the newly created custom role to your managed identity:
# Assign the custom role to the managed identity at directory scope
$managedIdentityPrincipalId = "<Your-User-Assigned-Managed-Identity-Principal-ID>"
$directoryScope = "/"
$roleAssignment = New-MgRoleManagementDirectoryRoleAssignment -DirectoryScopeId $directoryScope -PrincipalId $managedIdentityPrincipalId -RoleDefinitionId $customRole.Id
Step 3: Verify Custom Directory Role Assignment
Method 1: PowerShell Verification
# Verify the assignment
$verifyUri = "https://graph.microsoft.com/v1.0/roleManagement/directory/roleAssignments?`$filter=principalId eq '$managedIdentityPrincipalId'"
$assignments = az rest --method get --uri $verifyUri | ConvertFrom-Json
Write-Host "✓ Role assignment verification:" -ForegroundColor Green
$assignments.value | ForEach-Object {
Write-Host " - Role Definition ID: $($_.roleDefinitionId)" -ForegroundColor Cyan
Write-Host " - Directory Scope: $($_.directoryScopeId)" -ForegroundColor Cyan
Write-Host " - Principal ID: $($_.principalId)" -ForegroundColor Cyan
}
Method 2: Azure Portal Verification
You can also verify the custom directory role assignment through the Azure portal:
- Navigate to Azure Active Directory → Roles and administrators
- Search for your custom role: "EID SCIM Connector - Limited User Management"
- Click on the custom role name to open its details
- Go to Assignments in the left navigation menu
- Review the role assignments to confirm your managed identity is listed
You should see your managed identity assigned to the custom directory role as shown below:
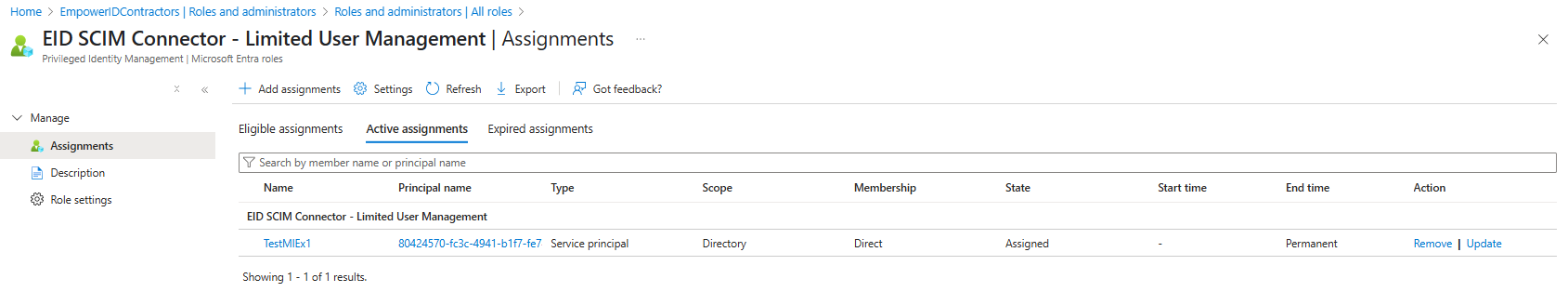
Create Azure RBAC Custom Role for Azure Resource Management
If you're managing Azure roles and management groups within EmpowerID, you’ll need to create an Azure RBAC custom role in addition to adding the necessary permissions in the script above. This custom role should include the required permissions, as outlined in the procedure below. Azure RBAC custom roles are used to govern access to Azure resources such as virtual machines, storage accounts, databases, and networking services. They are defined using Microsoft.* action sets and can be assigned at various scopes, including subscriptions, resource groups, or specific resources.
-
In Azure, navigate to the target subscription and select Access control (IAM) from the Azure navbar.
-
On the Access Control (IAM) page, click Add and select Add custom role.
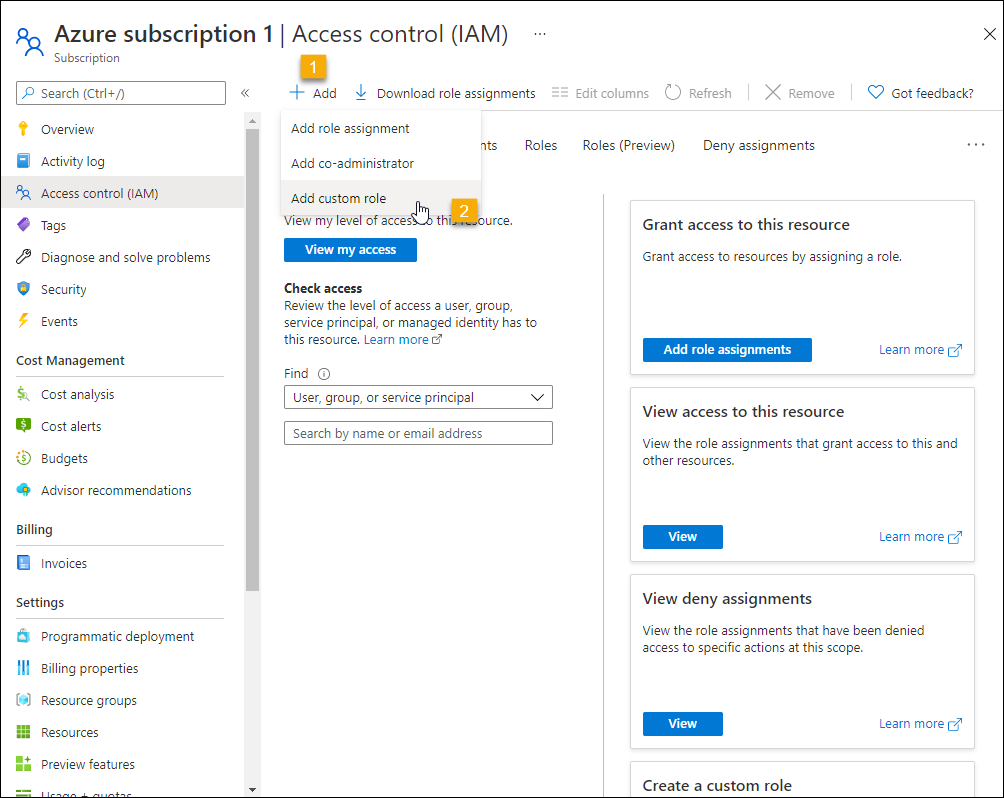
-
Under Basics, enter a Custom role name.
-
Select the Permissions tab and click Add permissions.
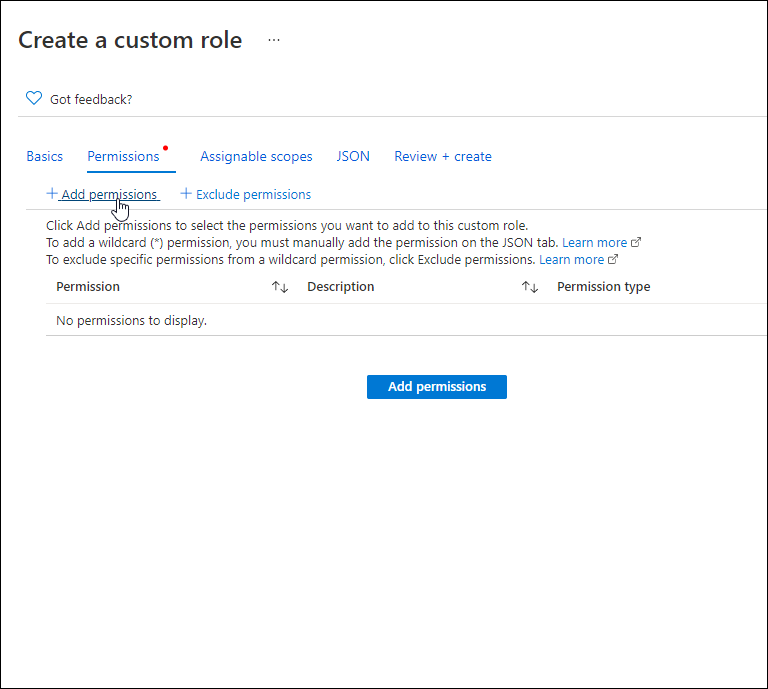
-
Search for Microsoft.ManagedIdentity and click the Microsoft Managed Identity tile.
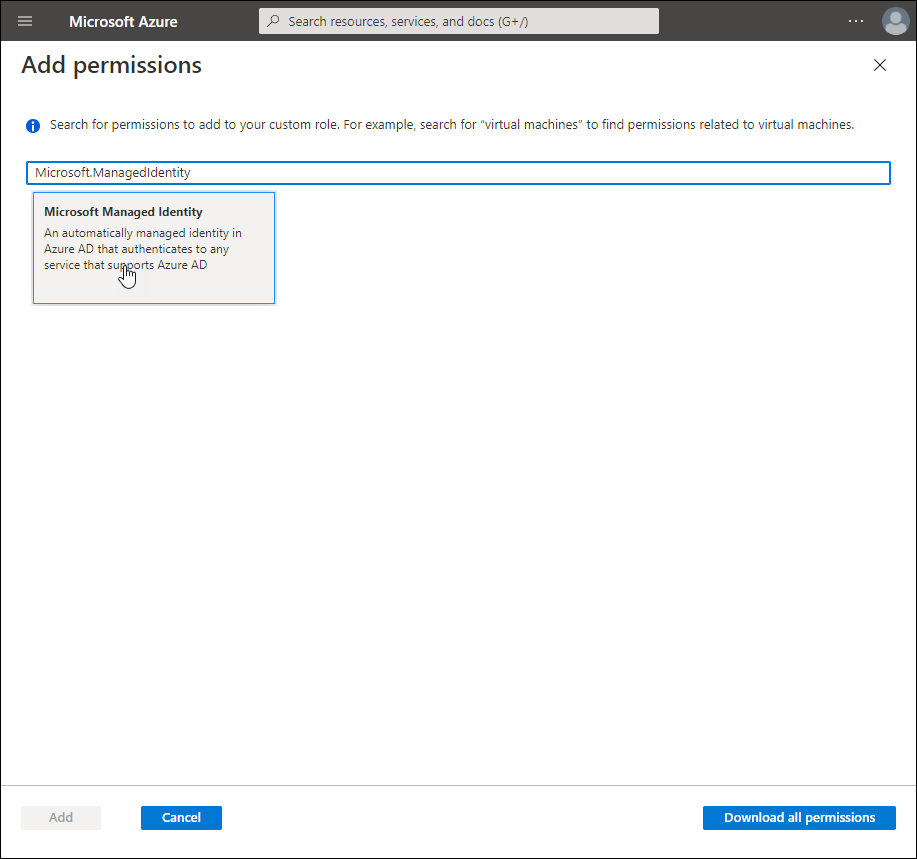
-
For Actions, under Microsoft.ManagedIdentity/userAssignedIdentities, select the following:
- Read : Get User Assigned Identity
- Write : Create/Update User Assigned Identity
- Delete : Delete User Assigned Identity
-
Click Add.
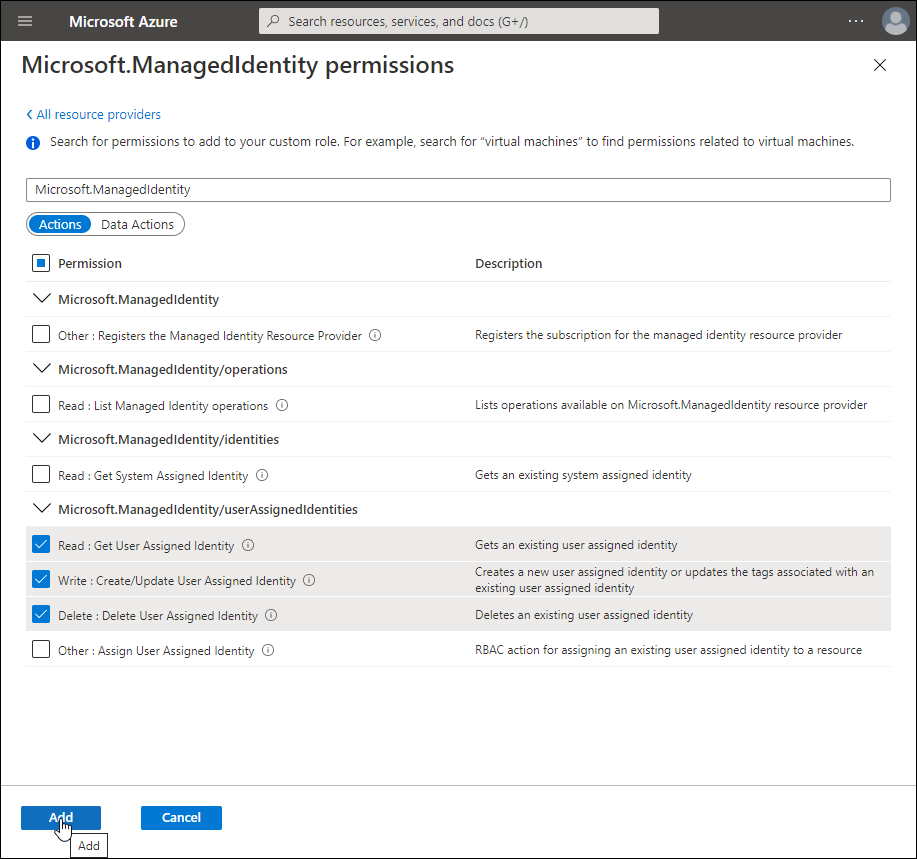
-
Back on the Create a custom role page, click Add permissions again and then search for Microsoft.Authorization.
-
Click the Microsoft Authorization tile and then add the below permissions:
-
Microsoft.Authorization/roleAssignments
-
Read : Get role assignment
-
Write : Create role assignment
-
Delete : Delete role assignment
-
-
Microsoft.Authorization/roleDefinitions
-
Read : Get role definition
-
Write : Create or update custom role definition
-
Delete : Delete custom role definition
-
-
-
Click Add.
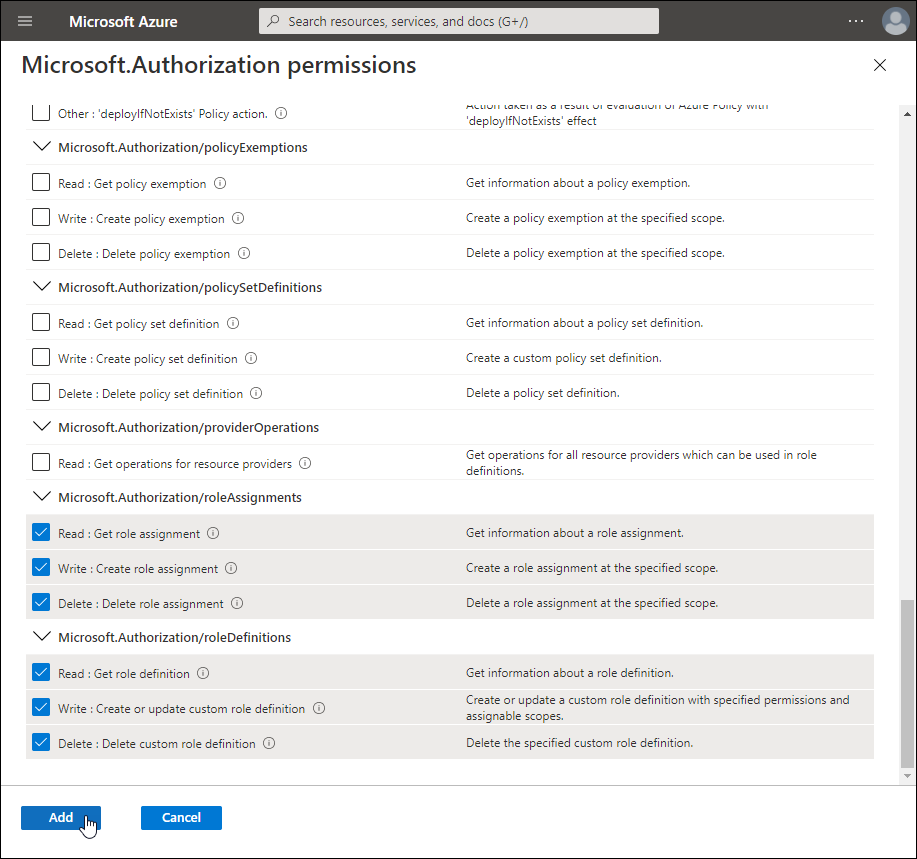
-
Back on the Create a custom role page, click Add permissions again and then search for Microsoft.Authorization.
-
Click the Microsoft Management tile and select Read : List Groups under Microsoft.Management/managementGroups.
-
Click Add.
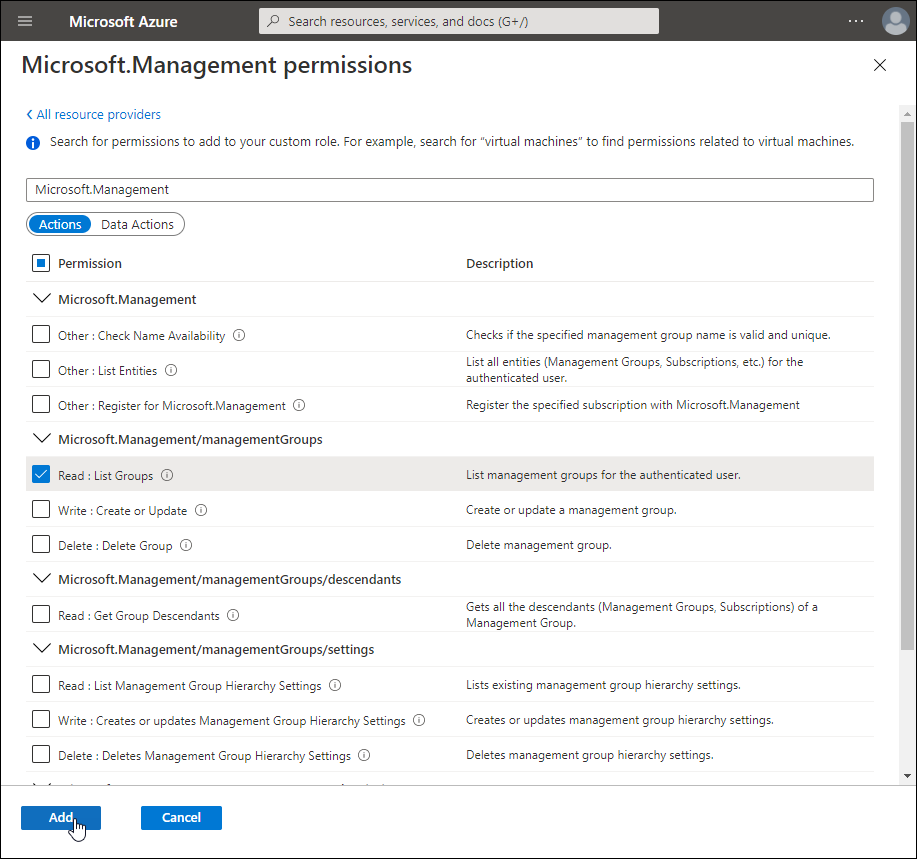
-
Back on the Create a custom role page, click Add permissions again, and then search for Microsoft.Resources.
-
Click the Microsoft Resources tile and then select the following permissions:
-
Microsoft.Resources/subscriptions/resourcegroups
- Read : Get Resource Group
-
Microsoft.Resources/subscriptions/resources
- Read : Get Subscription Resources
-
Microsoft.Resources/tenant
- Read : Get Tenants
-
-
Click Add.
-
Back on the Create a custom role page, select the Assignable scopes tab and verify the scope.
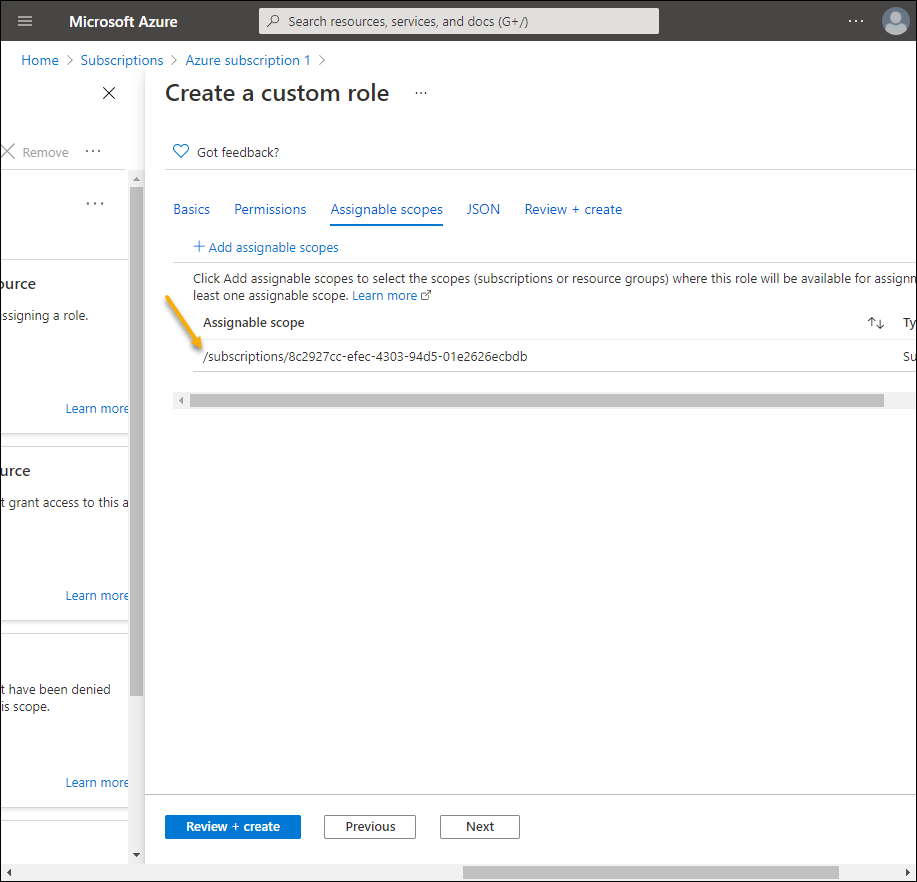
-
Click Review + Create.
-
Review the permissions and then click Create.
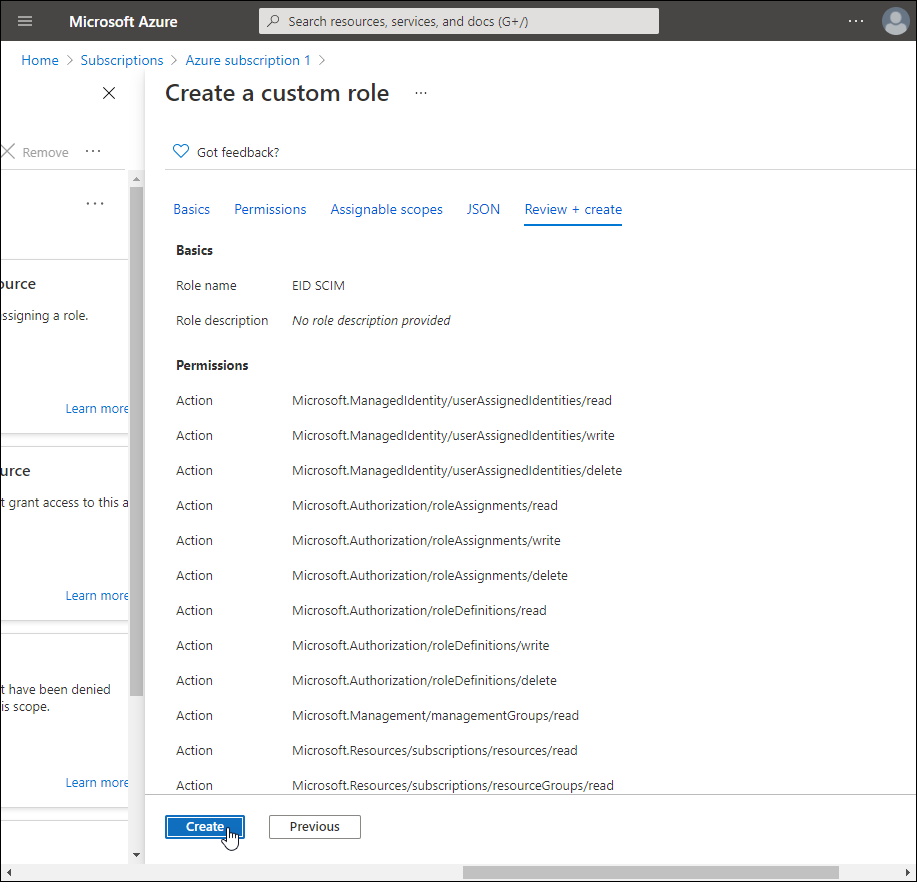
-
Click OK to close the "created custom role" message.
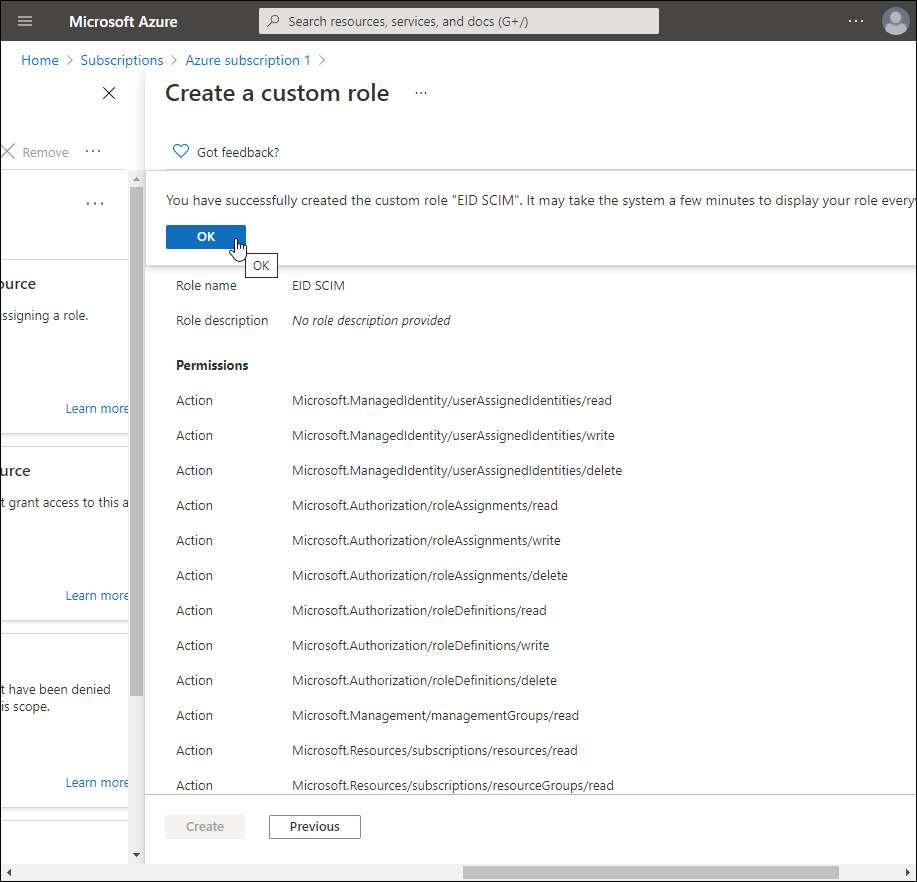
Now that you have created the custom role with the needed permissions, you need to assign the EntraID SCIM microservice to the role.
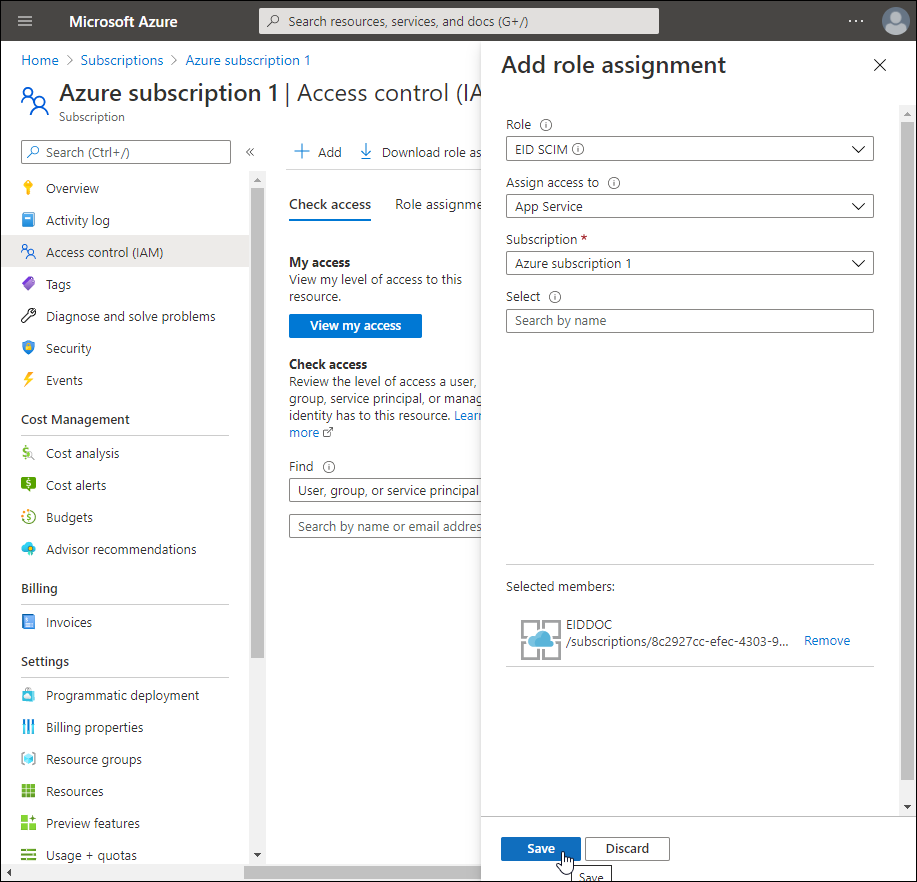
21. On the Access control (IAM) page, click Add > Add role assignment.
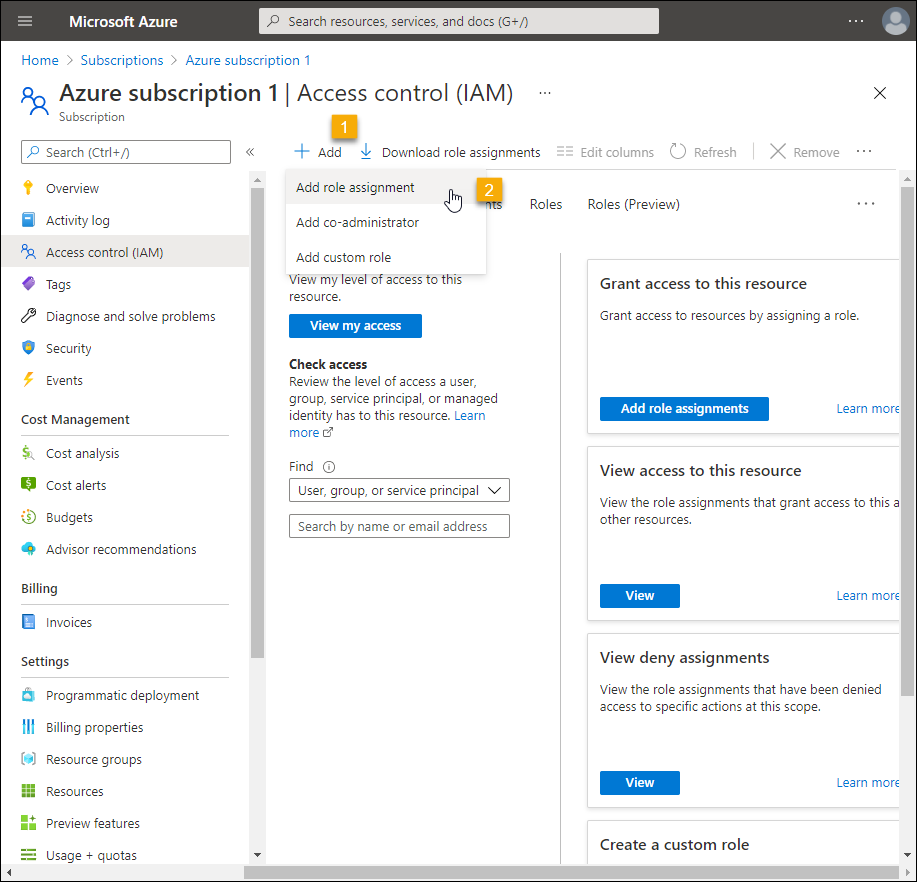 22. In the Add role assignment pane that appears, enter the following:
22. In the Add role assignment pane that appears, enter the following:
- Role – Select the custom role you just created
- Assign access to – App Service
- Subscription – Target subscription
- Select – The SCIM app service you created earlier.
- Click Save to add the role assignment.
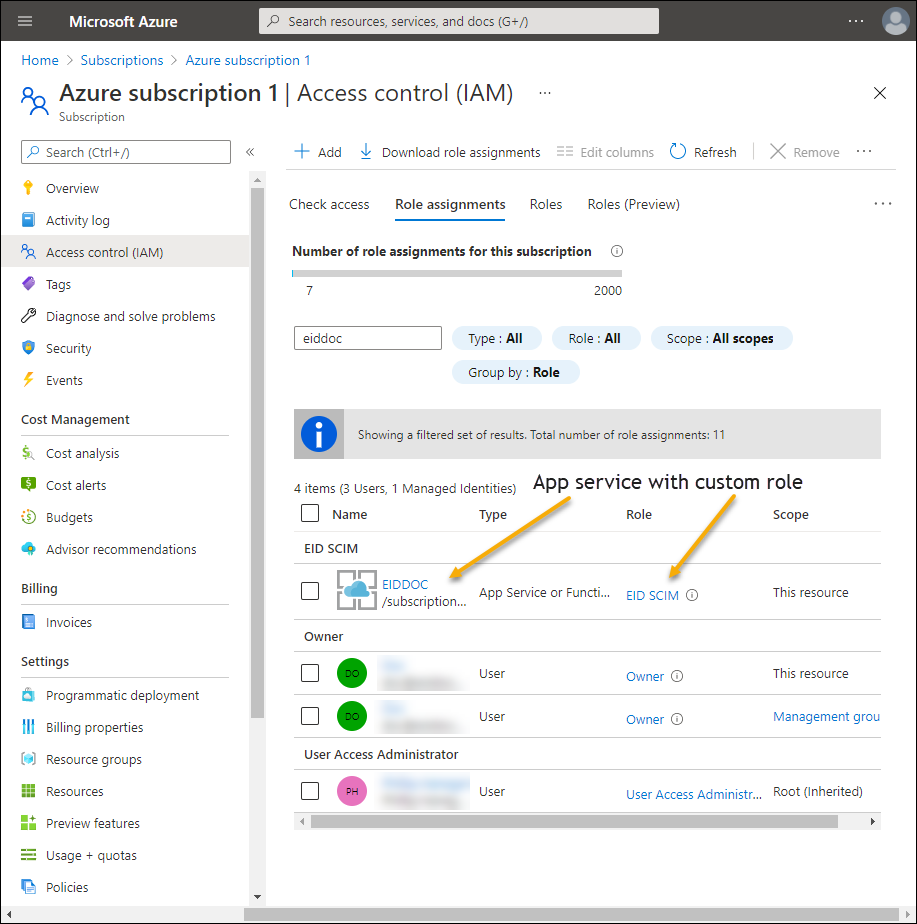
- On the Access control (IAM) page, select the Role assignments tab. You should see the SCIM app service you created assigned to the custom role.
Troubleshooting Permission Issues
Common Issues and Solutions:
Issue: "Insufficient privileges to complete the operation"
- Solution: Verify the specific permission required and ensure it's assigned
- Check: Confirm admin consent has been granted
Issue: "The user or administrator has not consented to use the application"
- Solution: Grant admin consent for the application permissions
- PowerShell:
Grant-AdminConsent -ApplicationId <app-id>
Issue: Custom role permissions not taking effect
- Solution: Allow up to 15 minutes for role assignments to propagate
- Check: Verify the role is assigned at the correct scope level
Appendix: Microsoft Graph API Permissions Reference
This appendix provides a comprehensive list of Microsoft Graph API Application Permissions required for each endpoint used in the EntraID SCIM Connector. These permissions represent the traditional tenant-wide approach, which grants broad access across all resources in your Azure tenant.
The permissions listed in the following tables represent traditional application-level permissions, but each can be replaced with an appropriate custom role definition when implementing the least-privilege approach.
User & Group Management
Endpoints related to user and group administration.
User Management
| Operation Description | Least Privileged Permissions |
|---|---|
| Create User | User.ReadWrite.All |
| Update/Delete User | User.ReadWrite.All |
| Get User by ID | User.Read.All |
| Get All Users | User.Read.All |
| Get All Deleted Users | Directory.Read.All |
| Get User Sign-In Activity | AuditLog.Read.All |
| Get Sign-Ins Log | AuditLog.Read.All |
| Reset User Password | UserAuthenticationMethod.ReadWrite.All |
| Revoke Sign-In Sessions | User.ReadWrite.All |
Group Management
| Operation Description | Least Privileged Permissions |
|---|---|
| Create Group | Group.ReadWrite.All |
| Update/Delete Group | Group.ReadWrite.All |
| Get Group by ID | Group.Read.All |
| Get All Groups | Group.Read.All |
| Get All Deleted Groups | Directory.Read.All |
| Get Group Members | Group.Read.All |
| Create Teams from Group | Group.ReadWrite.All, Team.ReadWrite.All |
Application & Service Principal Management
Endpoints for managing Applications and Service Principals.
Application Management
| Operation Description | Least Privileged Permissions |
|---|---|
| Create an Application | Application.ReadWrite.All |
| Delete or Update an Application | Application.ReadWrite.All |
| Get Application by ID | Application.Read.All |
| Get All Applications | Application.Read.All |
| Get Application Templates | Application.Read.All |
| Add Certificate to Application | Application.ReadWrite.All |
| Add Password to Application | Application.ReadWrite.All |
| Remove Certificate from Application | Application.ReadWrite.All |
| Remove Password from Application | Application.ReadWrite.All |
Service Principal Management
| Operation Description | Least Privileged Permissions |
|---|---|
| Create Service Principal | Application.ReadWrite.All |
| Delete or Update Service Principal | Application.ReadWrite.All |
| Get Service Principal by ID | Application.Read.All |
| Get All Service Principals | Application.Read.All |
| Manage App Role Assignments | AppRoleAssignment.ReadWrite.All |
Role & Permissions Management
Endpoints related to role assignments and directory role management.
| Operation Description | Least Privileged Permissions |
|---|---|
| Create/Delete Directory Role Assignment | RoleManagement.ReadWrite.Directory |
| Create/Delete Unified Role Assignment | RoleManagement.ReadWrite.Directory |
| Create Role Definition | RoleManagement.ReadWrite.Directory |
| Assign Role to User or Group | RoleManagement.ReadWrite.Directory |
| Get Role Assignments | RoleManagement.Read.All |
| Get Role Definitions | RoleManagement.Read.All |
Security & Conditional Access
Endpoints related to Conditional Access Policies and Security Attributes.
Conditional Access
| Operation Description | Least Privileged Permissions |
|---|---|
| Create Conditional Access Policy | Policy.ReadWrite.ConditionalAccess |
| Get Conditional Access Policies | Policy.Read.All |
| Delete Conditional Access Policy | Policy.ReadWrite.ConditionalAccess |
Custom Security Attributes
| Operation Description | Least Privileged Permissions |
|---|---|
| Create Security Attribute Definition | CustomSecAttributeDefinition.ReadWrite.All |
| Get or Update Security Attribute Definition | CustomSecAttributeDefinition.ReadWrite.All |
| Create Security Attribute Set | CustomSecAttributeDefinition.ReadWrite.All |
| Get or Update Security Attribute Set | CustomSecAttributeDefinition.ReadWrite.All |
| Assign/Remove Security Attributes for Users | CustomSecAttributeAssignment.ReadWrite.All |
| Assign/Remove Security Attributes for Service Principals | CustomSecAttributeAssignment.ReadWrite.All |
| Get All Security Attribute Assignments for Users | CustomSecAttributeAssignment.Read.All |
| Get All Security Attribute Assignments for Service Principals | CustomSecAttributeAssignment.Read.All |
Directory & Subscription Management
Endpoints for managing Azure Directory and Subscriptions.
| Operation Description | Least Privileged Permissions |
|---|---|
| Get Tenant Details | Directory.Read.All |
| Get Subscriptions | Directory.Read.All |
| Update/Delete Subscription | Directory.ReadWrite.All |
Special Section: Azure-Specific Permissions
Some endpoints require Azure Role-Based Access Control (RBAC) permissions in addition to Graph API permissions. These permissions are specifically for managing Azure resources, roles, and management groups. They are different from the Microsoft Graph API permissions and need to be configured separately in Azure.
| Operation Description | Required Azure Role Permissions |
|---|---|
| Get Tenants | Microsoft.Resources/tenants/read |
| Get Subscriptions | Microsoft.Resources/subscriptions/read |
| Get Management Groups | Microsoft.Management/managementGroups/read |
| Get Resources | Microsoft.Resources/resources/read |
| Create/Delete Resource Group | Microsoft.Resources/subscriptions/resourcegroups/write |
| Get/Delete Classic Administrators | Microsoft.Authorization/classicAdministrators/read |
| Read Role Assignments | Microsoft.Authorization/roleAssignments/read |
| Write Role Assignments | Microsoft.Authorization/roleAssignments/write |
| Delete Role Assignments | Microsoft.Authorization/roleAssignments/delete |
| Read Custom Role Definitions | Microsoft.Authorization/roleDefinitions/read |
| Write Custom Role Definitions | Microsoft.Authorization/roleDefinitions/write |
| Delete Custom Role Definitions | Microsoft.Authorization/roleDefinitions/delete |
| Update Role Assignment in Management Group | Microsoft.Authorization/roleDefinitions/write |
Reference: For more details, refer to Microsoft Graph Permissions Reference