Overview of EntraID SCIM Connector
The EmpowerID EntraID SCIM Connector provides organizations with a comprehensive solution for managing and synchronizing user, group, role, license, application, and other data hosted in their Azure Cloud. By integrating this data into EmpowerID, organizations can ensure consistent management and synchronization across all connected back-end user directories, enhancing their identity governance and access management capabilities.
Architecture Overview
The EmpowerID EntraID SCIM Connector's architecture is designed to securely interface with Azure Active Directory (EntraID), facilitating the management and synchronization of user identities, groups, roles, licenses, and related data. The architecture comprises several key components that interact to ensure seamless data exchange between EmpowerID and EntraID.
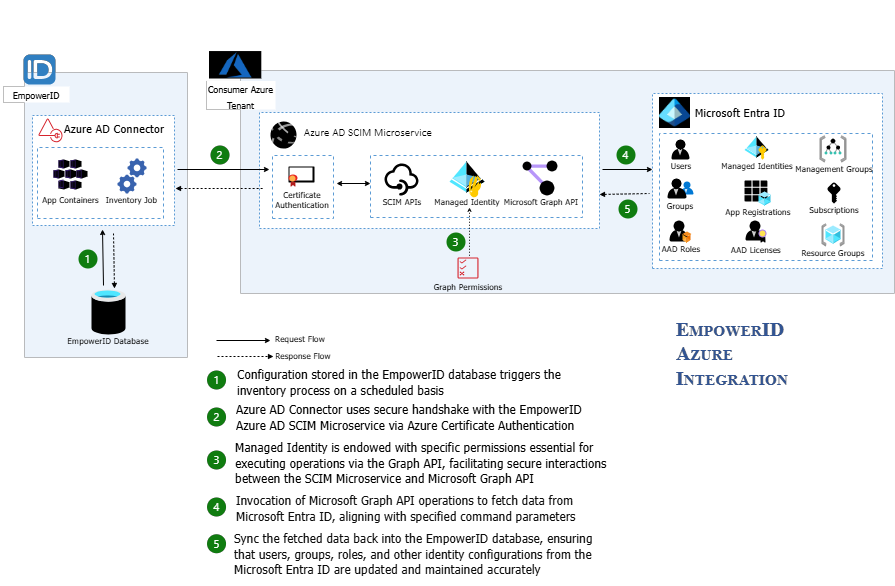
System Components and Data Flow
The EmpowerID EntraID SCIM Connector architecture comprises several key components that enable secure and efficient data exchange between EmpowerID and EntraID. Central to this architecture are the EmpowerID Web & App Server Containers, which host the necessary services and applications. These containers execute inventory and job tasks to collect and process data from EntraID, storing the results in the EmpowerID Identity Warehouse – an SQL-based database for managing user identities, groups, roles, and other related attributes.
The system uses certificate-based authentication to establish secure communication between EmpowerID and the EntraID tenant. This approach ensures that the EmpowerID EntraID SCIM App Service can interact securely with EntraID, maintaining data integrity and preventing unauthorized access.
The EmpowerID EntraID SCIM App Service is deployed within the customer's Azure tenant and serves as the interface between EmpowerID and EntraID. It utilizes the SCIM 2.0 protocol to manage and synchronize data. The App Service communicates with EntraID via the Microsoft Graph API, performing CRUD (Create, Read, Update, Delete) operations on resources such as users, groups, roles, and licenses.
In the Azure environment, the SCIM App Service uses a Managed Identity to interact securely with EntraID and other Azure services. Azure automatically manages managed identities, streamlining the authentication and authorization processes and eliminating the need for manual credential management.
The Microsoft Graph API allows the SCIM App Service to access and manipulate EntraID data directly. The service can retrieve and update user data, group memberships, roles, licenses, and other critical resources through the API, ensuring that the information is consistent across both EmpowerID and EntraID.
Secure Data Inventory and Management
The EmpowerID EntraID SCIM Connector offers several data management capabilities, allowing organizations to efficiently manage their EntraID resources within EmpowerID.
Account Management
- Inventory User Accounts: Collect and manage user account data from EntraID.
- Create, Update, and Delete User Accounts: Perform CRUD operations on user accounts directly from EmpowerID.
- Enable and Disable User Accounts: Manage the active status of user accounts.
- Reset User Account Passwords: Initiate password resets for user accounts.
Group Management
- Inventory Groups and Group Memberships: Collect and manage group data, including membership details.
- Create and Delete Groups: Perform CRUD operations on groups within EntraID.
- Add and Remove Group Memberships: Manage user memberships within groups.
- Add or Remove Group Members: Directly manage individual users within group memberships.
Role Management
- Inventory Azure Roles and Role Memberships: Collect and manage role data and role memberships from EntraID.
- Create Azure RBAC and Custom Directory Roles: Define and manage RBAC roles and custom directory roles.
- Assign Users to Azure Roles: Assign or modify user roles directly within EmpowerID.
License Management
- Inventory License Bundles, License Pools, and Tenant Subscriptions: Collect and manage licensing data from EntraID.
- Add or Remove License Assignments for Users: Manage individual user license assignments.
- Add or Remove License Assignments for Groups: Manage group-based license assignments.
Application Management
- Inventory Azure Applications, Credentials, App Roles, Scopes, App Role Assignments, and Scope Assignments: Collect and manage application-related data.
- Create Azure OIDC, SAML (Non-Gallery), and SAML (Gallery) Applications: Define and manage different applications within EntraID.
- Edit and Delete Azure Applications: Perform CRUD operations on EntraID applications.
- Create and Delete Client Secrets and Certificates: Manage application secrets and certificates.
- Create and Delete Scopes and App Roles: Define and manage application scopes and roles.
- Update API Permissions and Token Configurations: Modify permissions and token settings for EntraID applications.
Data Synchronization and Lifecycle Management
Once data from EntraID is inventoried and mapped in EmpowerID, it becomes part of the platform's broader identity lifecycle management processes. The following sections outline how the connector handles data synchronization and supports key lifecycle events.
Data Synchronization
The EmpowerID EntraID SCIM Connector enables synchronization between EntraID and EmpowerID. This synchronization ensures that any changes made in EntraID, such as updates to user roles, group memberships, or application assignments, are promptly reflected in EmpowerID. Synchronization is bidirectional, meaning that updates made in EmpowerID can also be propagated back to EntraID if needed.
Lifecycle Management
The EmpowerID EntraID SCIM Connector integrates with EmpowerID's lifecycle management processes, allowing for seamless user, group, and role lifecycle management based on EntraID data. The following processes are supported:
- Provisioning: Automatically create new users, groups, and roles in EmpowerID based on EntraID data, ensuring these entities are assigned the correct attributes and access rights defined in EntraID.
- Updating: Synchronize changes made to existing users, groups, and roles in EntraID with EmpowerID, reflecting modifications such as role changes, group reassignments, or updates to user attributes across both systems.
- Deprovisioning: When users, groups, or roles are removed from EntraID, they can be automatically deprovisioned in EmpowerID. This process ensures that deactivated entities are appropriately handled, including removing access rights and deleting them as required.
Attribute Mapping
To ensure seamless integration, the EmpowerID EntraID SCIM Connector maps attributes from EntraID to the appropriate fields within EmpowerID. This mapping process ensures that all relevant data is captured and aligns with the data models used by EmpowerID. Below is an example of how key attributes are mapped:
| EntraID Attribue | EmpowerID Person Attribute |
|---|---|
| profileUrl | AboutMe |
| active | Active |
| phoneNumbers[?@.type=='work'].value | BusinessPhone |
| city | City |
| companyName | Company |
| employeeOrgData.costCenter | CostCenter |
| country | Country |
| usageLocation | CustomAttribute10 |
| ['urn:ietf:params:scim:schemas:extension:enterprise:2.0:User'].['department'] | Department |
| description | Description |
| employeeOrgData.division | Division |
| endDateTime | effectiveEndDate |
| startDateTime | EffectiveStartDate |
| emails[?@.type=='work'].value | |
| externalId | EmailAlias |
| ['urn:ietf:params:scim:schemas:extension:enterprise:2.0:User'].['employeeNumber'] | EmployeeID |
| employeeType | EmployeeType |
| ['urn:ietf:params:scim:schemas:extension:azureOnPremData:2.0:User'].['onPremisesExtensionAttributes'].['extensionAttribute1'] | ExtensionAttribute1 |
| ['urn:ietf:params:scim:schemas:extension:azureOnPremData:2.0:User'].['onPremisesExtensionAttributes'].['extensionAttribute10'] | ExtensionAttribute10 |
| ['urn:ietf:params:scim:schemas:extension:azureOnPremData:2.0:User'].['onPremisesExtensionAttributes'].['extensionAttribute11'] | ExtensionAttribute11 |
| ['urn:ietf:params:scim:schemas:extension:azureOnPremData:2.0:User'].['onPremisesExtensionAttributes'].['extensionAttribute12'] | ExtensionAttribute12 |
| ['urn:ietf:params:scim:schemas:extension:azureOnPremData:2.0:User'].['onPremisesExtensionAttributes'].['extensionAttribute13'] | ExtensionAttribute13 |
| ['urn:ietf:params:scim:schemas:extension:azureOnPremData:2.0:User'].['onPremisesExtensionAttributes'].['extensionAttribute14'] | ExtensionAttribute14 |
| ['urn:ietf:params:scim:schemas:extension:azureOnPremData:2.0:User'].['onPremisesExtensionAttributes'].['extensionAttribute15'] | ExtensionAttribute15 |
| ['urn:ietf:params:scim:schemas:extension:azureOnPremData:2.0:User'].['onPremisesExtensionAttributes'].['extensionAttribute2'] | ExtensionAttribute2 |
| ['urn:ietf:params:scim:schemas:extension:azureOnPremData:2.0:User'].['onPremisesExtensionAttributes'].['extensionAttribute3'] | ExtensionAttribute3 |
| ['urn:ietf:params:scim:schemas:extension:azureOnPremData:2.0:User'].['onPremisesExtensionAttributes'].['extensionAttribute4'] | ExtensionAttribute4 |
| ['urn:ietf:params:scim:schemas:extension:azureOnPremData:2.0:User'].['onPremisesExtensionAttributes'].['extensionAttribute5'] | ExtensionAttribute5 |
| ['urn:ietf:params:scim:schemas:extension:azureOnPremData:2.0:User'].['onPremisesExtensionAttributes'].['extensionAttribute6'] | ExtensionAttribute6 |
| ['urn:ietf:params:scim:schemas:extension:azureOnPremData:2.0:User'].['onPremisesExtensionAttributes'].['extensionAttribute7'] | ExtensionAttribute7 |
| ['urn:ietf:params:scim:schemas:extension:azureOnPremData:2.0:User'].['onPremisesExtensionAttributes'].['extensionAttribute8'] | ExtensionAttribute8 |
| ['urn:ietf:params:scim:schemas:extension:azureOnPremData:2.0:User'].['onPremisesExtensionAttributes'].['extensionAttribute9'] | ExtensionAttribute9 |
| phoneNumbers[?@.type=='fax'].value | Fax |
| name.givenName | FirstName |
| displayName | FriendlyName |
| name.honorificSuffix | GenerationalSuffix |
| phoneNumbers[?@.type=='home'].value | HomeTelephone |
| name.familyName | LastName |
| userName | Login |
| manager | ManagerPersonID |
| name.middleName | MiddleName |
| phoneNumbers[?@.type=='mobile'].value | MobilePhone |
| addresses[?@.type=='other'].formatted | Office |
| externalAudience | OofAudience |
| scheduledEndDateTime | OofEndDate |
| externalReplyMessage | OofExternalMsg |
| internalReplyMessage | OofInternalMsg |
| scheduledStartDateTime | OofStartDate |
| status | OofStatus |
| photos[?@.type=='work'].value | PhotoURL |
| addresses[?@.type=='work'].postalCode | PostalCode |
| preferredLanguage | PreferredLanguage |
| state | State |
| addresses[?@.type=='work'].streetAddress | StreetAddress |
| phoneNumbers[?@.type=='other'].value | Telephone |
| title | Title |
Permissions and Configuration
For detailed information about the Microsoft Graph API permissions required for the EntraID SCIM Connector and step-by-step configuration guidance, please refer to the Assign Permissions to the App Service documentation.
The permissions guide provides:
- Complete Microsoft Graph API permission requirements for all connector operations
- Implementation approaches for both tenant-wide and least-privilege permission models
- Step-by-step configuration instructions with PowerShell scripts
- Verification methods and troubleshooting guidance