Create a Claims Mapping Policy in EmpowerID
Claims mapping policies control what user information is sent to an Azure application after sign-in. Applications can then use this data—such as roles, departments, or group membership—to determine what the user is allowed to do.
This guide shows you how to create a reusable claims mapping policy in EmpowerID using the Create Microsoft Entra Claims Mapping Policy workflow in the Resource Admin app.
Claims added to a policy are reused across applications. To configure claims for a single app, use the Manage Azure App Wizard instead.
What You'll Need
| Requirement | Description |
|---|---|
| Access | You must have permission to access applications in Resource Admin and manage policies for your Azure tenant. |
| Tenant Access | The Azure tenant must already be registered in EmpowerID. |
Steps to Create a Claims Mapping Policy
1. Launch the Create Claims Mapping Policy Workflow
- Navigate to the portal for the Resource Admin app in your environment.
- Log in using your credentials.
If you don’t know the direct URL to Resource Admin, contact your EmpowerID administrator.
- From the dropdown menu, select Applications, then click the Workflows tab.
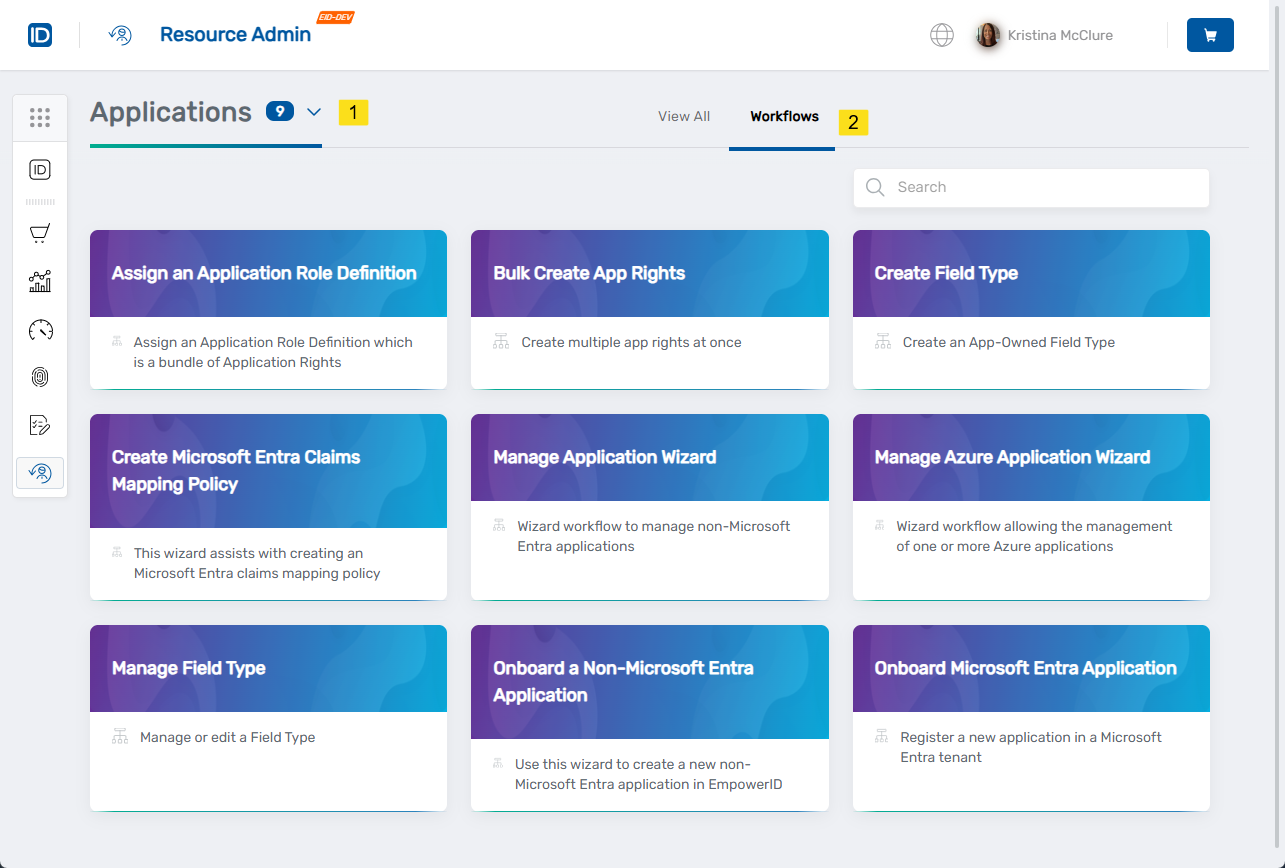
- Search for
CreateAzureClaims, then click the Create Microsoft Entra Claims Mapping Policy workflow tile.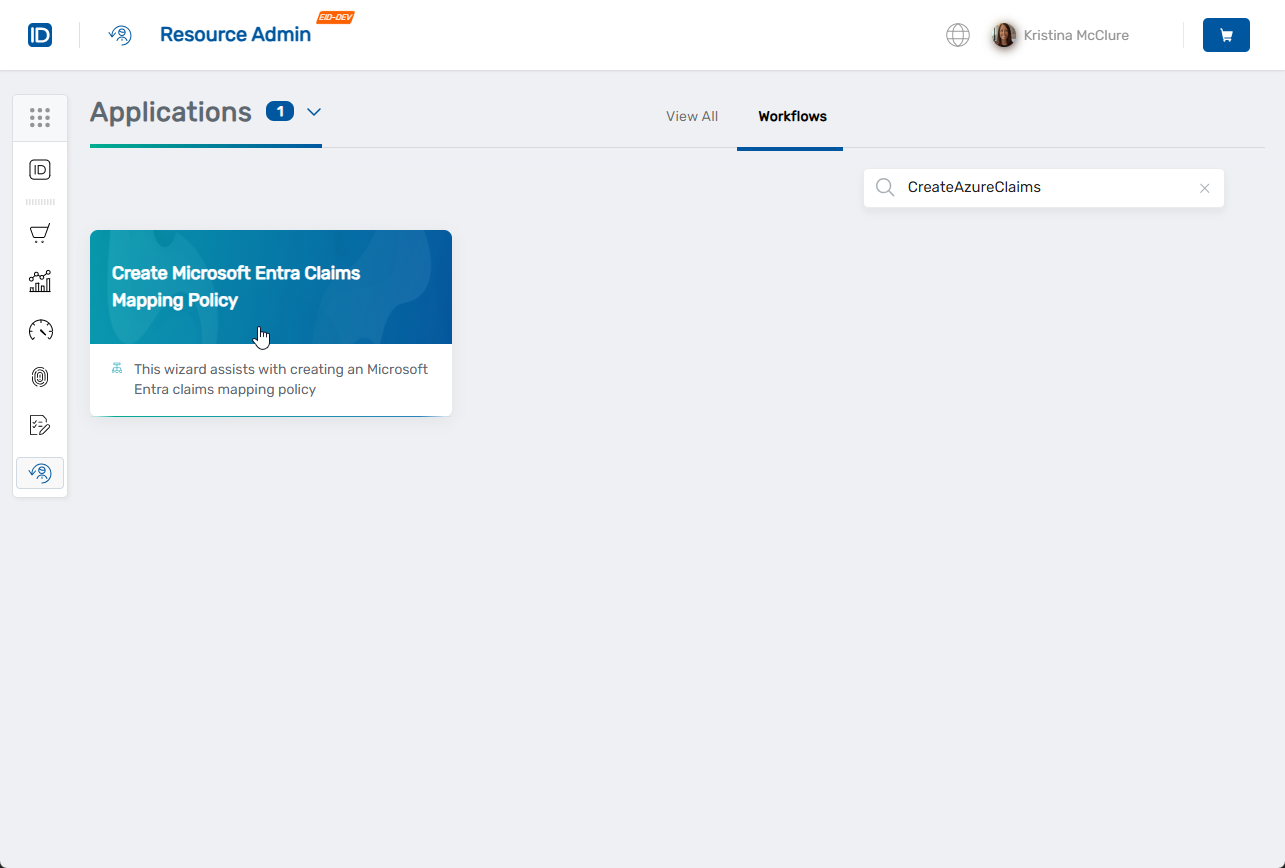
2. Enter Tenant and Policy Details
The workflow opens to the Tenant & Policy Details screen.
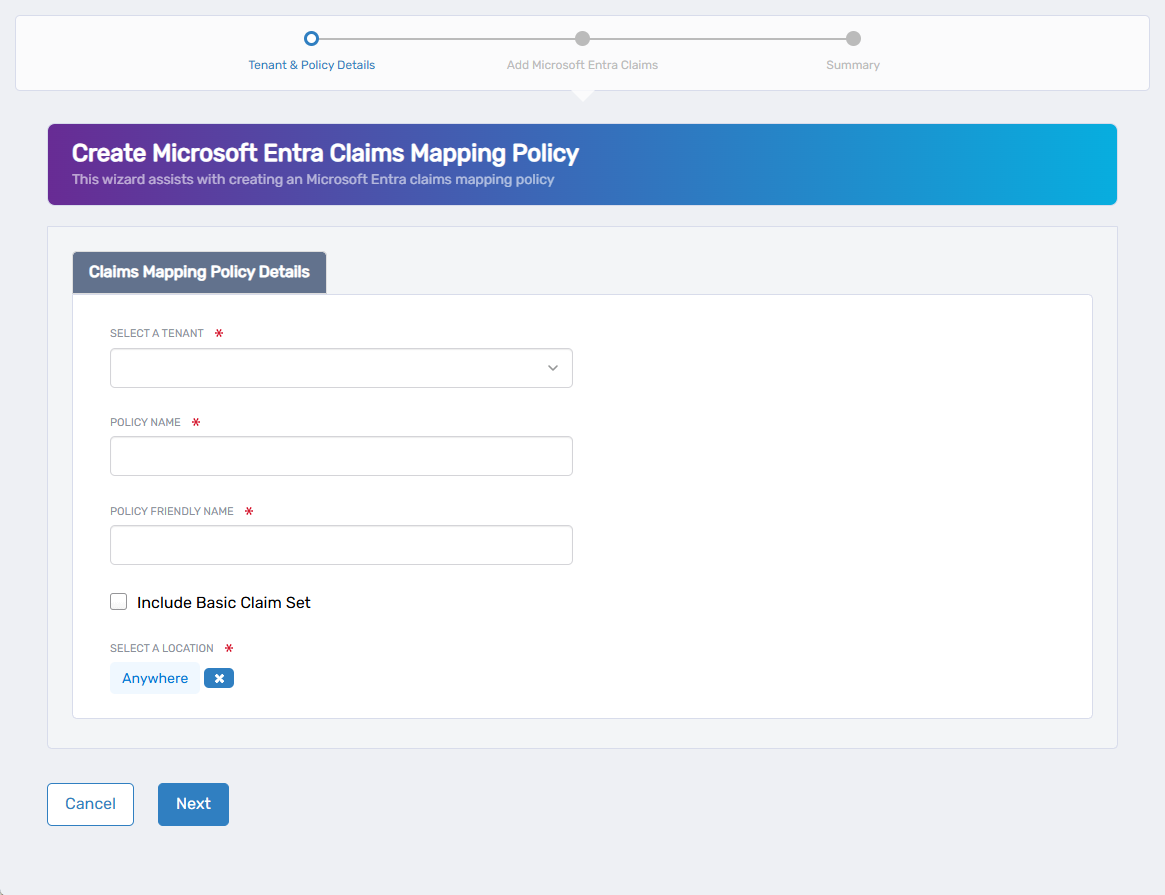
- Complete the following fields:
- Select a Tenant – Choose the Azure tenant the policy applies to.
- Policy Name – Enter a unique internal identifier.
- Policy Friendly Name – Enter a display name for the UI.
- Include Basic Claim Set – Check to automatically include standard claims like user ID, email, and display name.
- Select a Location – Choose an RBAC location for policy delegation.
If a default location is pre-filled and needs to be changed, click the (X) next to the field and then click Select a Location to search.
- Click Next to proceed.
If you click Back before clicking Next, your changes on this step will be lost.
3. (Optional) Add Source Claims
The wizard continues to the Add Microsoft Entra Claims screen with the Source Claims tab open.
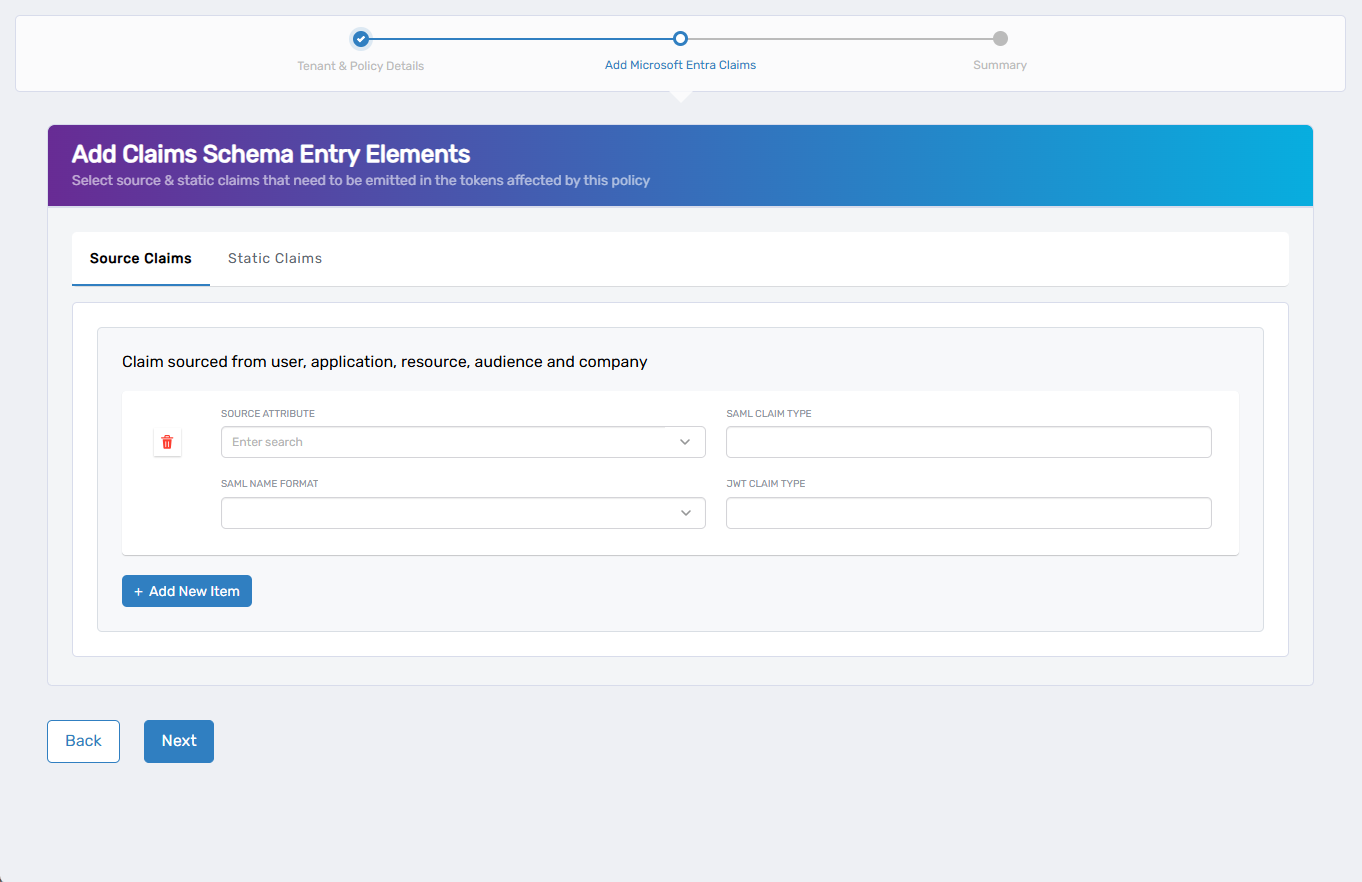
Use this step to add dynamic claims based on user, application, or resource attributes.
- Click + Add New Item to add a new row.
- Complete the following fields:
| Field | Description |
|---|---|
| Source Attribute | Azure attribute to use as the value (e.g., user.mail) |
| SAML Claim Type | Claim type expected by SAML applications |
| SAML Name Format | Name format such as emailAddress or unspecified |
| JWT Claim Type | Claim name for JWT tokens (e.g., email) |
- Repeat to add more claims as needed.
- When finished, either:
- Click the Static Claims tab to add static values, or
- Click Next to skip static claims and continue.
If you click Back before clicking Next, your changes on this step will be lost.
4. (Optional) Add Static Claims
Use this screen to define static (hardcoded) claims that always emit the same value.
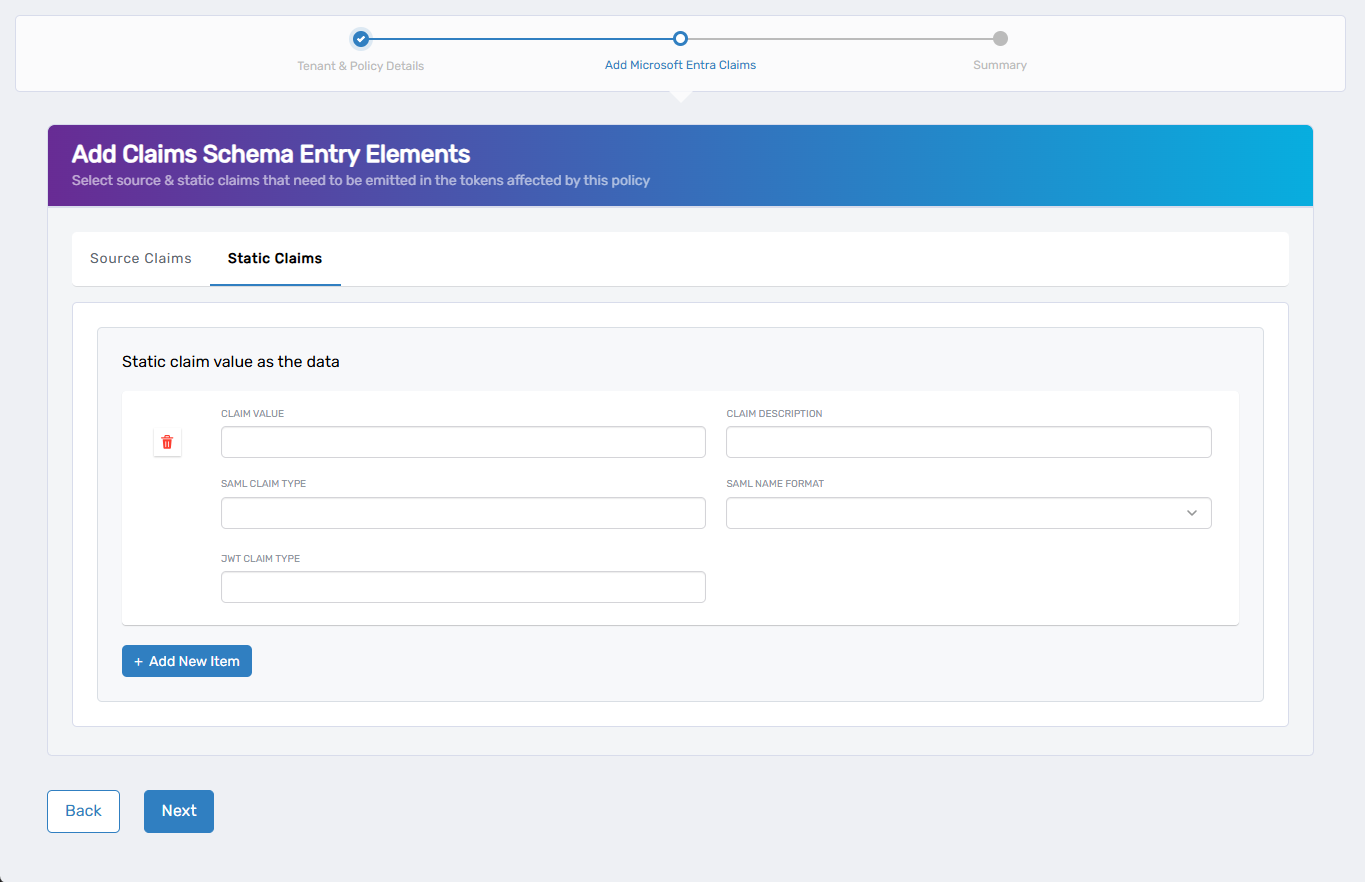
- Click + Add New Item.
- Complete the following fields:
| Field | Description |
|---|---|
| Claim Value | The static value to include (e.g., true, Engineering) |
| Claim Description | (Optional) Friendly label to help identify the claim |
| SAML Claim Type | SAML claim type used by apps expecting SAML tokens |
| SAML Name Format | Format such as emailAddress, unspecified, etc. |
| JWT Claim Type | JWT claim name for token output |
- Repeat to add more static claims if needed.
- Click Next to proceed.
If you click Back before clicking Next, your changes on this step will be lost.
5. Review and Submit
The summary screen appears.
- Review your selections and claims for accuracy.
- If changes are needed, click Back.
- When ready, click Submit to create the policy.
You will see a confirmation message upon success.
6. Verify the Policy
- From the Applications dropdown, select Claims Mapping Policies.
- Search for the policy name.
- Click Details to confirm the configuration.
What Happens Next
- Your new policy can now be assigned to one or more Microsoft Entra applications.
- Claims in the policy will be emitted to tokens for those apps once assigned.