Overview of the EmpowerID GCP Connector
The Google SCIM Connector enables organizations to integrate EmpowerID with Google Cloud Platform (GCP) for centralized identity management. Through this integration, EmpowerID can inventory and synchronize user and group identity-related information stored within Google Cloud environments, ensuring seamless identity governance across various backend directories.
Overview
The EmpowerID Google Cloud Platform (GCP) Connector securely inventories and manages identity data within Google Cloud using the EmpowerID SCIM 2.0 Microservice. This microservice, deployed in Google App Engine, facilitates direct data exchange between EmpowerID and Google Cloud by processing requests initiated by the connector.
Currently, the GCP Connector supports the following services:
- Google Workspace
- Google Cloud
GCP Connector Environment
This section provides an overview of the key components involved in integrating GCP with EmpowerID, explaining their roles, interactions, and data flow processes.
Major Components
Several components work together to ensure secure and efficient identity synchronization between EmpowerID and Google Cloud Platform (GCP). Below is a breakdown of their functions and interactions:
Google Cloud Platform (GCP) Connector
The GCP Connector serves as a bridge between EmpowerID and Google Cloud. It initiates requests that EmpowerID needs to execute within GCP. For example, if a user creates a group in EmpowerID, the GCP Connector triggers the necessary API requests to create the group in GCP. Additionally, it includes inventory logic to track identity changes. If a group is created directly in GCP, the connector updates EmpowerID accordingly, based on the output received from the SCIM Microservice.
GCP SCIM Microservice
The GCP SCIM Microservice acts as an intermediary between EmpowerID and Google Cloud. It receives and processes requests from the GCP Connector, executing them through Google Cloud APIs. This microservice is:
- Deployed in Google App Engine
- Responsible for transforming requests from the connector into API calls
- SCIM 2.0-compliant, ensuring standardized communication
Identity-Aware Proxy (IAP)
Google Cloud’s Identity-Aware Proxy (IAP) secures access by authenticating and authorizing requests from the GCP Connector and GCP SCIM Microservice. Only requests with verified OIDC tokens are processed, ensuring security and controlled access.
Google Cloud API
The Google Cloud API serves as the interface for executing identity-related tasks within GCP. The SCIM Microservice calls these APIs to perform actions such as:
- Creating and disabling users
- Managing groups and fetching group memberships
GCP Connector Data Flow
The following section outlines how different components interact to automate identity management tasks in GCP from EmpowerID.
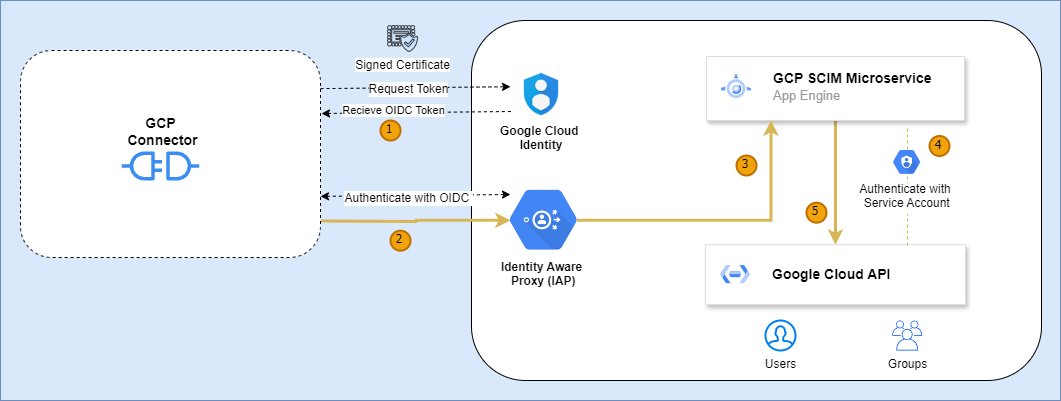
1. GCP Connector Requests Token & Authentication
- The GCP Connector sends a request to the Google Authentication Service, using OAuth 2.0 for authentication and authorization.
- This request is signed with a certificate, which is the private key of a service account stored in EmpowerID.
2. Token Issuance
- The Google Authentication Service validates the request and issues an OpenID Connect (OIDC) bearer token.
- This token contains the service account's identity and its granted permissions.
3. IAP Authentication
- The OIDC bearer token is verified by Identity-Aware Proxy (IAP).
- The IAP ensures the token’s scope and audience match the SCIM Microservice before allowing access.
4. Microservice Access Granted
- Once authenticated, the GCP Connector is granted access to the SCIM Microservice, which is protected by IAP.
- This ensures that only authorized requests are forwarded to the microservice.
5. Microservice Authentication with GCP API
- The SCIM Microservice authenticates with Google Cloud APIs using a service account assigned the necessary roles and permissions.
6. API Call Execution
- The SCIM Microservice, acting with the permissions of the service account, performs API calls to manage users and groups in Google Cloud.
- Supported operations include:
- Creating and disabling users
- Managing groups and retrieving group members