Overview of the CyberArk SCIM Connector
The CyberArk SCIM Connector facilitates integration between EmpowerID and CyberArk environments. It enables EmpowerID to inventory and manage user and group identity information stored in CyberArk. This centralized management capability allows seamless synchronization of identity processes across various backend directories.
The connector leverages EmpowerID's native SCIM capabilities for secure data inventory and management within CyberArk.
CyberArk Connector Environment
This section outlines the components and data flow of integrating EmpowerID with CyberArk.
Key Components
-
CyberArk SCIM Connector: Core to the EmpowerID environment, the connector initiates requests to execute identity operations in CyberArk, such as creating groups. It also tracks identity changes between the two systems.
-
Base SCIM Connector & CyberArk Implementation: This implementation leverages CyberArk's SCIM-compliant interface to enable seamless integration with EmpowerID's Base SCIM connector system. The CyberArk SCIM Connector inherits from EmpowerID's Base SCIM connector with customizations specific to CyberArk environments.
-
OAuth 2.0 Authentication: Ensures secure authorization of requests with authentication tokens.
-
CyberArk APIs: Acts as the primary interface for executing identity-related operations, including inventory synchronization.
Data Flow Process
The CyberArk SCIM Connector is a specialized class library that inherits from the Base SCIM Connector within EmpowerID. While the Base SCIM Connector provides fundamental SCIM operations and authentication methods, the CyberArk SCIM Connector extends these capabilities with CyberArk-specific implementation
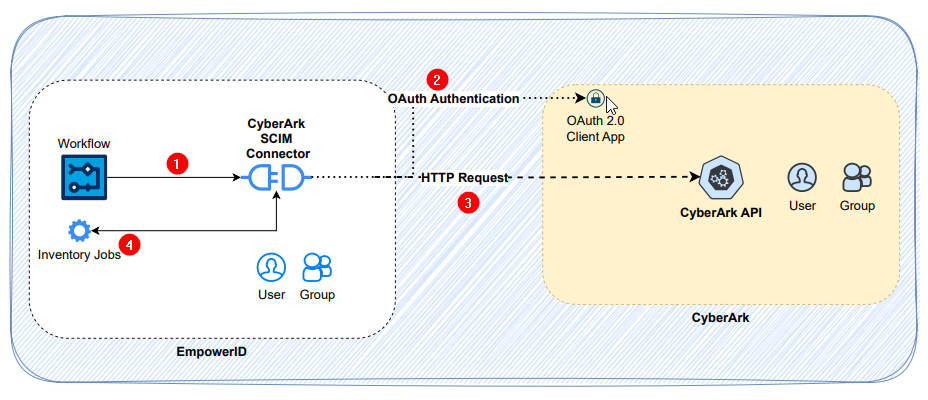
1 - Request Processing
When users perform actions in EmpowerID or any workflow that initiates a request for CyberArk, the Cyberark SCIM Connector initiates corresponding operations. The CyberArk SCIM connector is an integrated component rather than an independent deployed entity. It generates SCIM-compliant requests with the Base SCIM connector's inherited capabilities, which then transforms these actions into standardized API calls formatted according to CyberArk's API specifications.
2 - Authentication and Authorization
The CyberArk SCIM connector implements the OAuth 2.0 protocol for secure access management. For the connector to function properly, an OAuth2 client application with the necessary administrative rights must be configured in the CyberArk instance. If scopes are configured, they must be added to the resource system config settings. CyberArk administrators configure authentication applications with specific permission sets to control access levels. During access requests, the CyberArk SCIM connector obtains access tokens directly from the CyberArk endpoint by authenticating with client credentials, enabling subsequent identity management operations.
3 - API Communication
HTTP requests are directed to appropriate CyberArk API endpoints where necessary operations are performed. The SCIM connector processes these responses from the CyberArk API and makes them available to EmpowerID workflows and other components. This integration enables centralized management of CyberArk resources alongside other IAM resources within EmpowerID.
4 - Data Synchronization
The connector maintains data consistency through a robust inventory synchronization process between EmpowerID and CyberArk. This synchronization occurs during scheduled inventory operations. During these cycles, the connector performs a complete data refresh, ensuring that all changes made in either system are accurately reflected in the other. The connector implements a full inventory strategy for each synchronization job, as CyberArk's architecture does not support differential or incremental updates. In cases where synchronization encounters failures, the system employs an automatic retry mechanism that triggers during the next scheduled synchronization window, ensuring data integrity is maintained even in the face of temporary disruptions.
Administrators can monitor these inventory jobs through EmpowerID's interface and adjust scheduling parameters to optimize performance and resource utilization for their specific environment.
CyberArk Connector Authentication
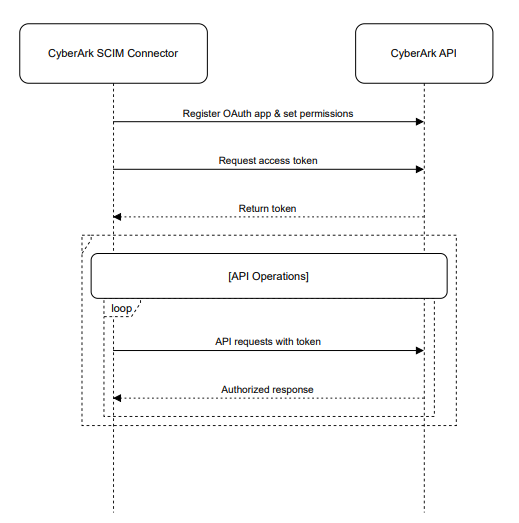
- Application Registration: Administrators register an OAuth application and define required scopes and permissions.
- Token Exchange: The CyberArk SCIM connector obtains an access token by authenticating with CyberArk's OAuth endpoint using client credentials. The credentials are stored securely in EmpowerrID, which the user configures while creating the account store.
- Access Token Usage: API requests to CyberArk include the token for authorization, ensuring secure operations.
- Token Renewal: The Cyberark SCIM connector manages token expiration by refreshing tokens to maintain continuous connectivity.