Overview of Adaptive Multi-Factor Authentication
Multi-Factor Authentication (MFA) is a security mechanism that requires users to provide at least two distinct forms of verification—typically something they know (e.g., password) and something they have (e.g., token or mobile device)—to access sensitive systems or data. This significantly reduces risks associated with compromised credentials.
EmpowerID implements a sophisticated Adaptive MFA engine that supports this security practice across multiple authentication contexts, including:
- Web SSO (Single Sign-On)
- LDAP
- RADIUS
Unlike static MFA, Adaptive MFA dynamically analyzes contextual data—such as IP address, device type, login location, time since last login, and velocity traveled—to determine the appropriate security response.
If EmpowerID identifies elevated risk, it enforces a stronger second factor before granting access.
Supported MFA Methods (Types)
EmpowerID supports a wide range of MFA methods, also referred to as MFA Types, including:
- DUO Push
- YubiKey
- One-time passwords (delivered via SMS, email, or voice)
- Other custom-configured tokens
Adaptive MFA vs. Standard MFA
EmpowerID includes both Adaptive MFA and traditional Standard MFA Policies. Both approaches leverage EmpowerID’s flexible, points-based system, also known as the Level of Assurance (LoA) framework.
MFA Points and Trust Model
EmpowerID allows administrators to assign trust points to various authentication-related entities, including:
- MFA methods
- IP address ranges
- Identity Providers
- Password Manager policies
Users must accumulate the configured number of trust points to successfully authenticate. For example, internal users might require fewer points than external users, and additional biographic verification may be required based on policy.
Standard MFA Scenario Diagram
The image below illustrates a typical EmpowerID MFA flow using trust point-based policies:
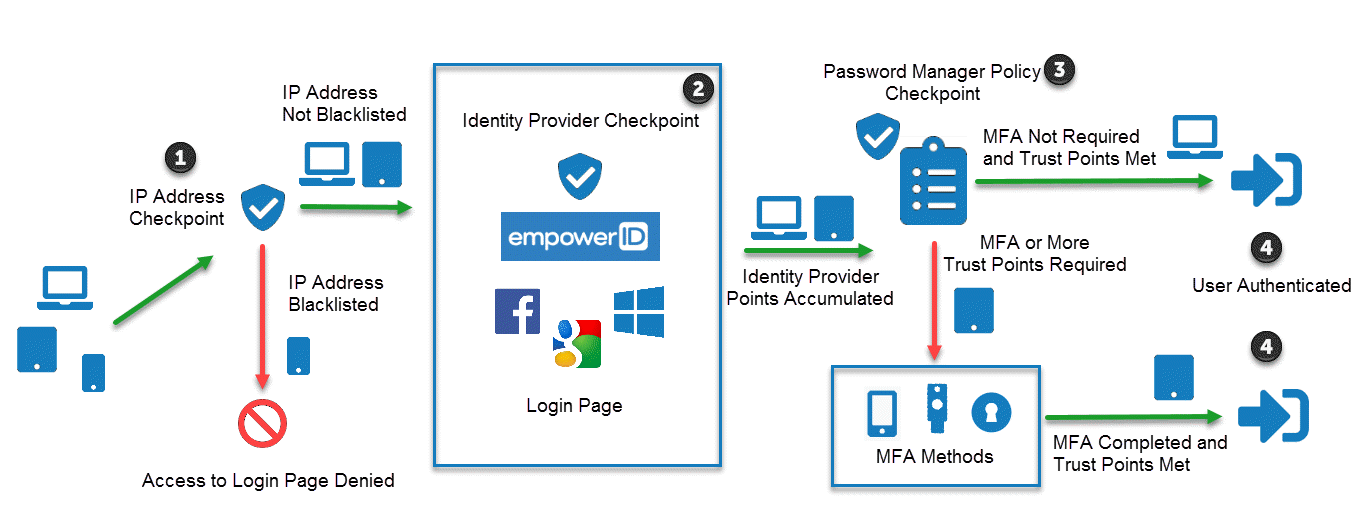
Scenario Flow Breakdown
-
IP Address Checkpoint
- Devices from blacklisted IP ranges are denied access to the Login page.
- In the diagram, a mobile phone is blocked at this stage.
-
Identity Provider Checkpoint
- Devices from non-blacklisted IP ranges (e.g., laptops and tablets) are allowed to proceed.
- Users select an available Identity Provider and submit credentials.
- EmpowerID assigns trust points associated with the selected Identity Provider.
-
Password Manager Policy Checkpoint
- EmpowerID evaluates each user’s assigned Password Manager policy.
- Based on the MFA requirements defined in the policy:
- The laptop user is authenticated immediately.
- The tablet user is required to complete an MFA challenge before access is granted.
Adaptive MFA Checkpoints in Detail
EmpowerID’s Adaptive MFA engine uses three main checkpoints to evaluate authentication attempts.
IP Address Checkpoint
This is the first gate in the authentication flow.
EmpowerID evaluates the source IP address against predefined IP Address Ranges, which administrators configure as part of the Adaptive MFA strategy.
IP Address Range Types
| Type | Description |
|---|---|
| Internal | IPs within the internal corporate network. |
| External | IPs outside of the internal network (e.g., internet-facing). |
| Blacklisted | IPs known to be malicious or unauthorized, denied access outright. |
Use Cases
- Require 1 trust point for internal IPs; 2+ trust points for external IPs.
- Allow Windows Auth only for internal users.
- Define public IPs for partner orgs to restrict login to Remote Windows IdP only.
- Allow external users to authenticate using EmpowerID Forms Auth and/or social logins.
- Deny access from blacklisted IPs completely.
If no IP address ranges are defined, EmpowerID treats all login attempts as external. This can affect authentication if trust point requirements differ between internal and external sources.
Identity Provider Checkpoint
This is the second gate users must pass after reaching the login page.
EmpowerID allows you to configure trusted OAuth 2.0 Identity Providers that users can authenticate with. Trust points can be assigned based on the Identity Provider selected.
Predefined Identity Provider Templates
EmpowerID includes templates for the following OAuth consumer applications:
- ADFS
- Azure
- Box
- EmpowerID OAuth
- EmpowerID Mobile OAuth
- Github
- Microsoft Live
- Paypal
- Salesforce
- SmartCard
- Windows Auth
- Yahoo
- Yammer
For custom integrations, EmpowerID also provides a generic OAuth template.
For detailed steps on assigning MFA types to identity provider applications, refer to
Assigning MFA Types to Applications.
Password Manager Policy Checkpoint
This is the final checkpoint before access is granted.
Password Manager Policies define:
- Authentication restrictions
- Password complexity rules
- Self-service password reset capabilities
- Enrollment and MFA requirements
Each policy specifies trust point thresholds for login attempts originating from:
- Local subnets (internal)
- Remote subnets (external)
Depending on the total trust points accumulated by the user (from IP and Identity Provider checkpoints), EmpowerID either:
- Grants access directly
- Prompts for additional MFA verification based on the defined policy
Administrators can configure:
- Default policies for the enterprise
- Group- or user-specific custom policies
Summary
EmpowerID’s Adaptive Multi-Factor Authentication framework offers a robust, context-aware approach to access security by combining:
- IP-based risk analysis
- Federated Identity Provider evaluation
- Password policy enforcement
The points-based Level of Assurance system provides administrators fine-grained control over how, when, and where users authenticate—ensuring compliance, reducing risk, and enhancing identity governance.