FIDO2 WebAuthn
FIDO2 WebAuthn is a W3C standard that utilizes public-key cryptography and digital signatures to eliminate password-based vulnerabilities. EmpowerID leverages this technology to enable:
- Multi-Factor Authentication (MFA) – Username + Password + FIDO2 credential
- Passwordless Login – Username + FIDO2 credential + PIN or biometric
- Usernameless Login – FIDO2 resident key + PIN or biometric (no username entry)
User security keys must support FIDO2.
System Configuration
Configure System Settings
-
Navigate to: Infrastructure Admin > EmpowerID Servers and Settings > EmpowerID System Settings
-
Search and configure the following settings:
System Setting Description FIDO2UsernamelessLoginEnabled Enables the Usernameless login option on the login screen. OathTokenIssuerName Sets the FIDO2 server name (e.g., ClientName-Dev,ClientName-UAT).MaximumRegisteredAssetsPerPersonPerType Limits the number of FIDO2 credentials a user can register. Default: 3.
Policy Configuration
Enable WebAuthn on Password Manager Policies
- Go to: Password Management > Password & Login Policies
- In the Policies tab, search for the desired policy.
- Click the Display Name link for that policy.
- On the policy View page, click Edit.
- Select the appropriate WebAuthn capability under the Authentication Settings tab in the Default FIDO2 Registration Capability field.
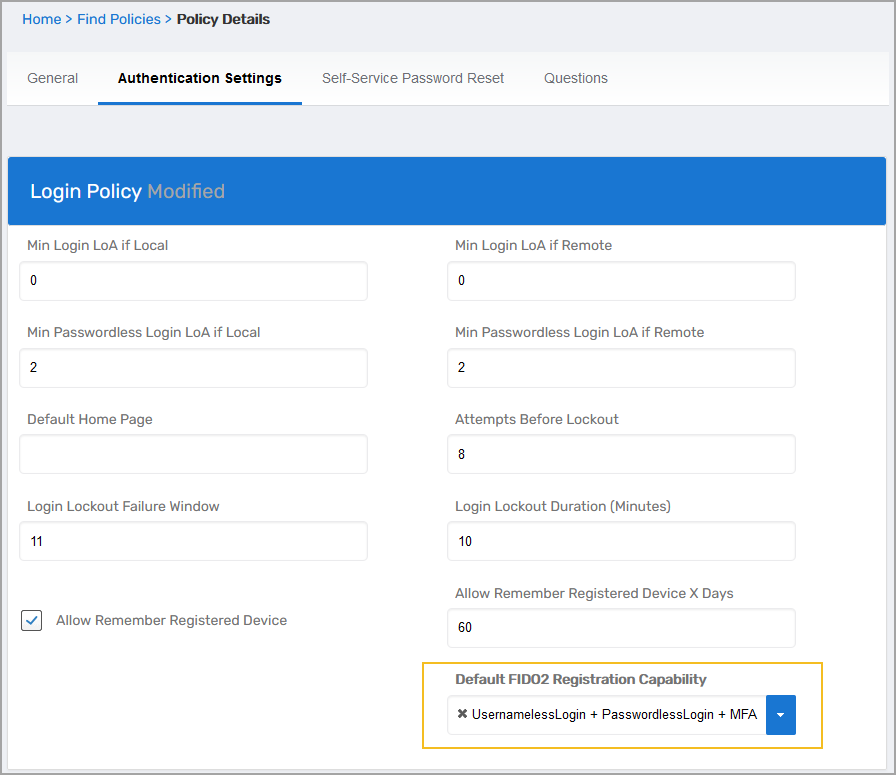
- Click Save to apply changes.
Device Management
Manage Registered FIDO2 WebAuthn Tokens
- Navigate to: Apps and Authentication > MFA Devices
- Search for FIDO2 to display registered devices.
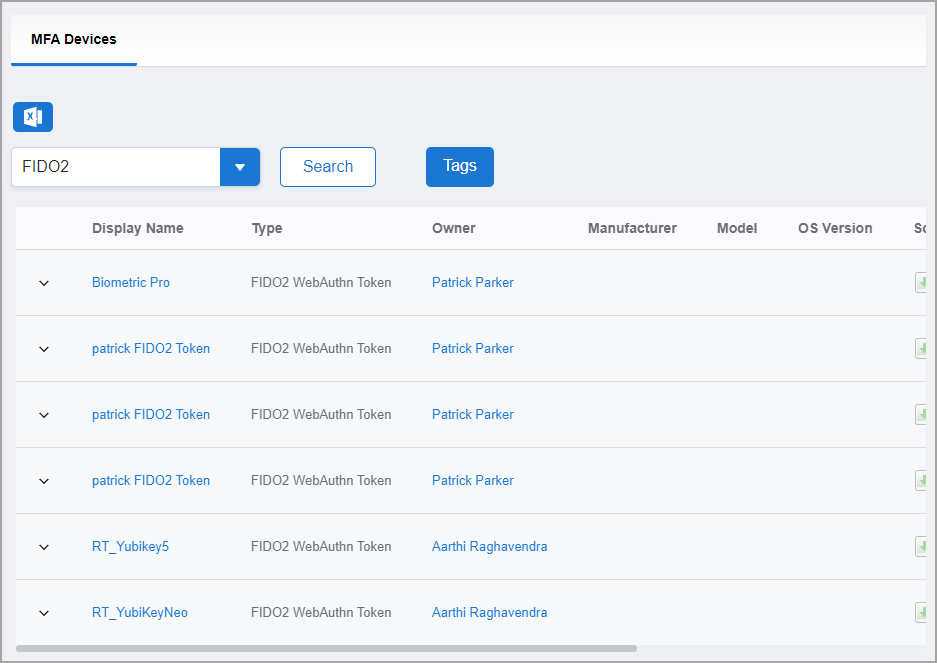
- Expand a token using the dropdown arrow.
- Choose one of the following actions:
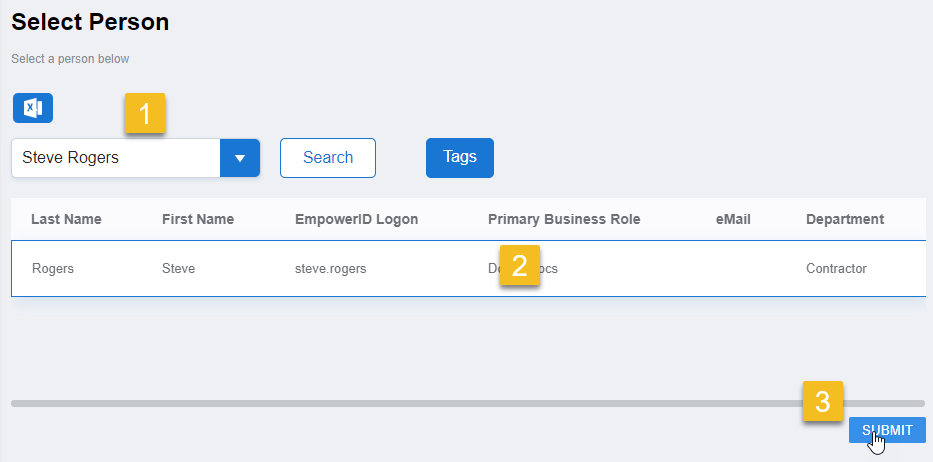
Assign Token to Person
- Click Assign Token To Person.
- Search for and select the user.
- Click Submit.
Delete Token
- Click Delete Asset.
- Confirm deletion.
User Experience
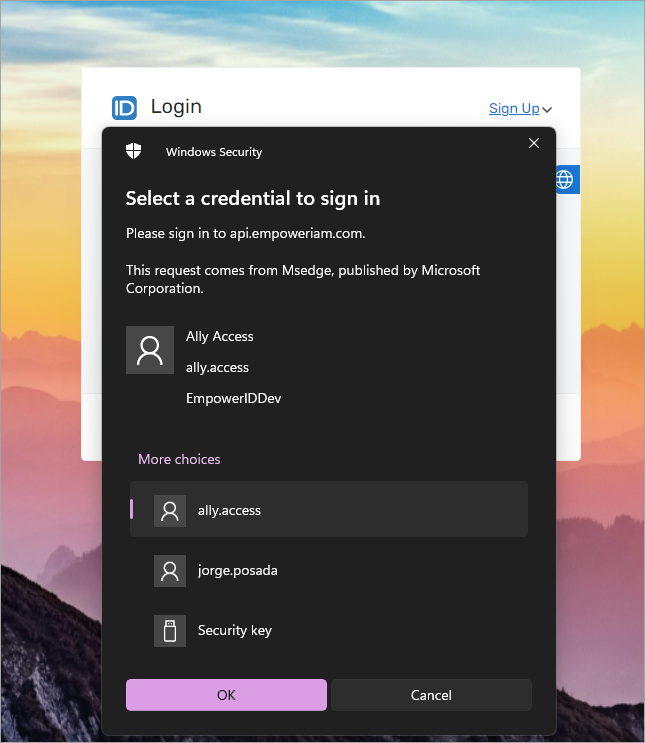
MFA FIDO2
Flow: Username + Password + FIDO2 Credential
When MFA FIDO2 is enabled, the authenticator can only be used as a second factor.
- First Login (Registration):
- Security Key: User touches the key.
- Laptop/PC: User enters PIN or biometric (fingerprint, FaceID).
- Subsequent Logins:
- Security Key: Touch required.
- Laptop/PC: PIN or biometric required.
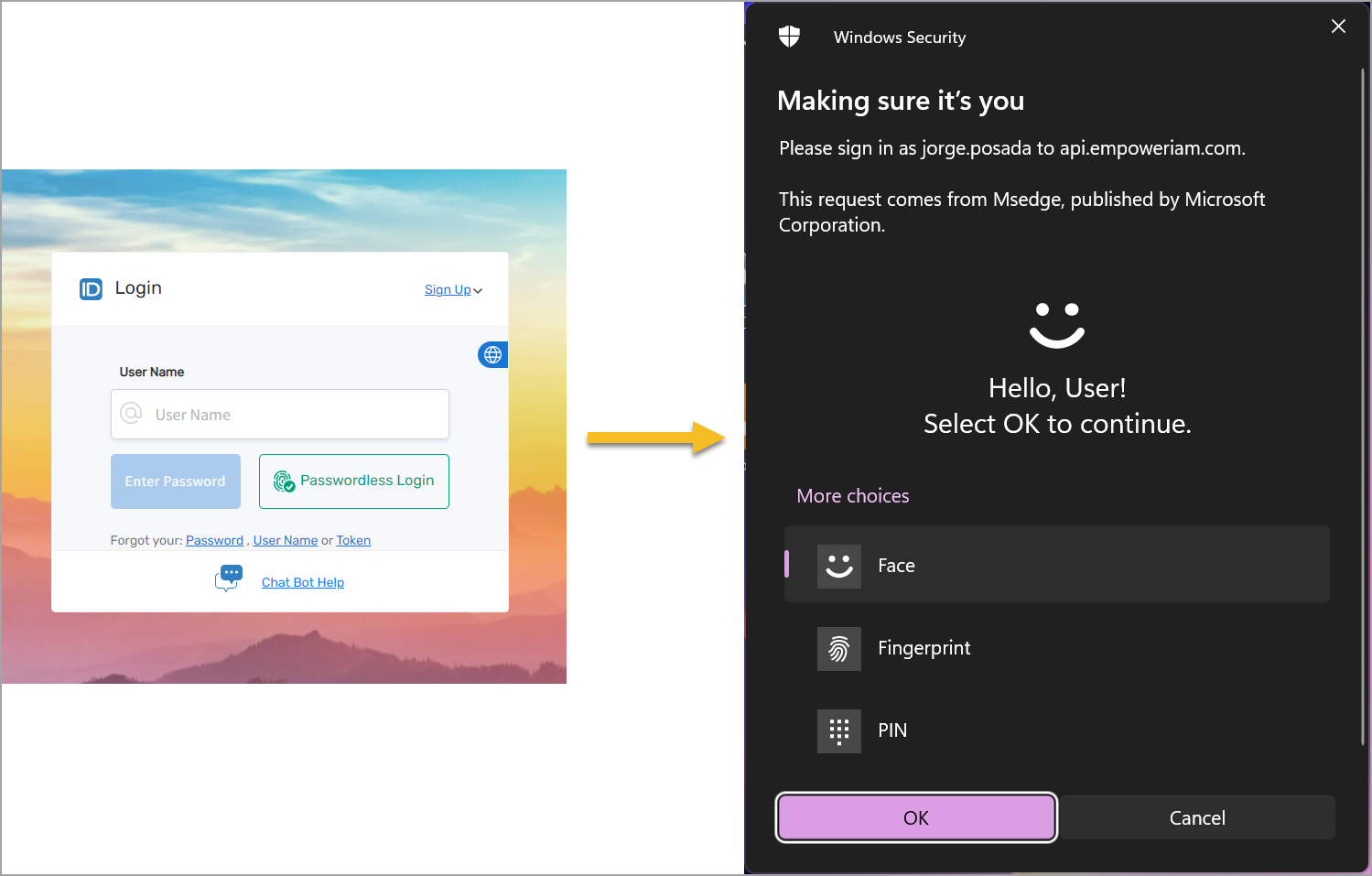
Sign-In Flow Experience
PasswordlessLogin FIDO2
Flow: Username + FIDO2 Credential + PIN/Biometric
When enabled, this capability supports both passwordless login and second-factor usage.
- First Login (Registration):
- Security Key: Touch + PIN/Biometric.
- Laptop/PC: PIN/Biometric.
- Login Workflow:
- Enter username.
- Complete authenticator action.
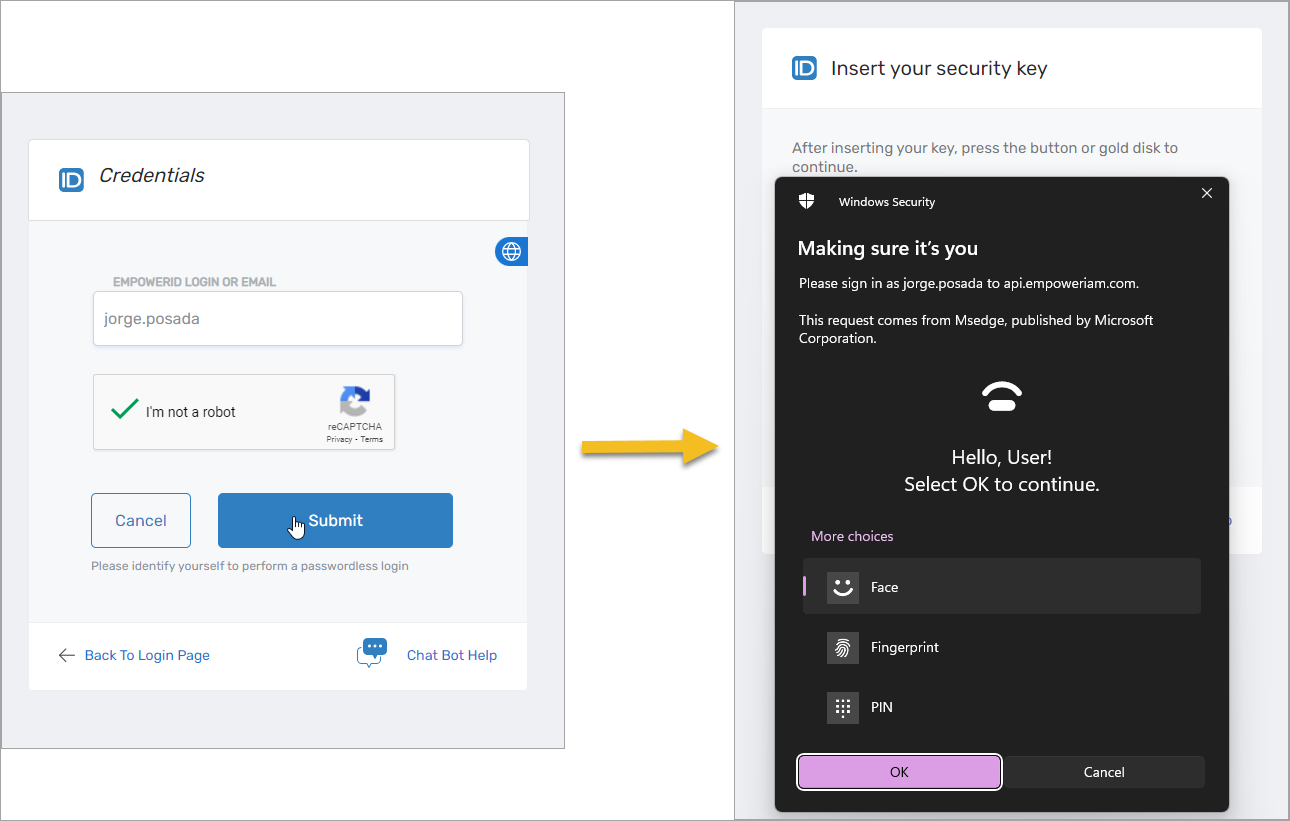
PasswordlessLogin Flow Experience
UsernamelessLogin FIDO2
Flow: FIDO2 Credential (Resident Key) + PIN/Biometric
Supports UsernamelessLogin, PasswordlessLogin, and second-factor authentication.
- First Login (Registration):
- Security Key: Resident key is generated and linked to domain (e.g.,
sso.empoweriam.com); user touches key + enters PIN/biometric. - Laptop/PC: Resident credential is generated; user enters PIN/biometric.
- Security Key: Resident key is generated and linked to domain (e.g.,
- Next Login:
- Device prompts automatically for PIN/biometric.
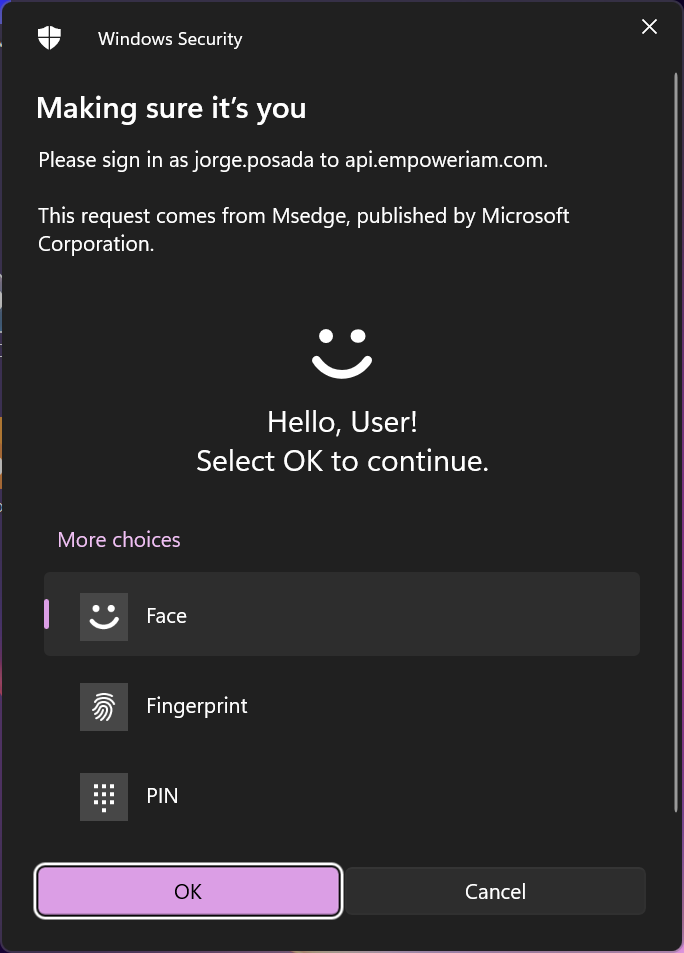
- Device prompts automatically for PIN/biometric.
Special Features / Use Cases
- A single FIDO2 Authenticator device can be associated with more than one identity.
- A single identity can have a maximum of
MaximumRegisteredAssetsPerPersonPerTypeFIDO2 devices. - If a FIDO2 authenticator associated with more than one identity is presented, EmpowerID will prompt the user to choose the identity for login.
- Users can run the
RegisterFido2Authenticatorworkflow to register additional devices.
Security and Compliance Notes
- Audit Logs: All registration and assignment actions are logged.
- Key Material: Private keys are never stored; only public keys are retained securely.
- Revocation: Deleting a token immediately revokes its authentication ability.
- Biometric Privacy: Biometric data is stored locally on the device and never transmitted.