Onboarding PBAC Applications
The Onboard Application workflow enables application owners and administrators to integrate PBAC and non-Azure applications into EmpowerID. This wizard-driven process includes configurable parameters, approval settings, and IAM Shop integration to align with your organization's security policies.
Prerequisites��
Before onboarding a PBAC application, ensure you have:
- Access to Resource Admin with the Application RBAC Owner Management Role (or higher)
- Application authorization model determined (PBAC vs non-PBAC)
- Owner and responsible party information identified
Procedure
-
Sign in to Resource Admin with at least the Application RBAC Owner Management Role.
-
Under "Applications," select the Workflows tab and click Onboard a Non-Azure Application.
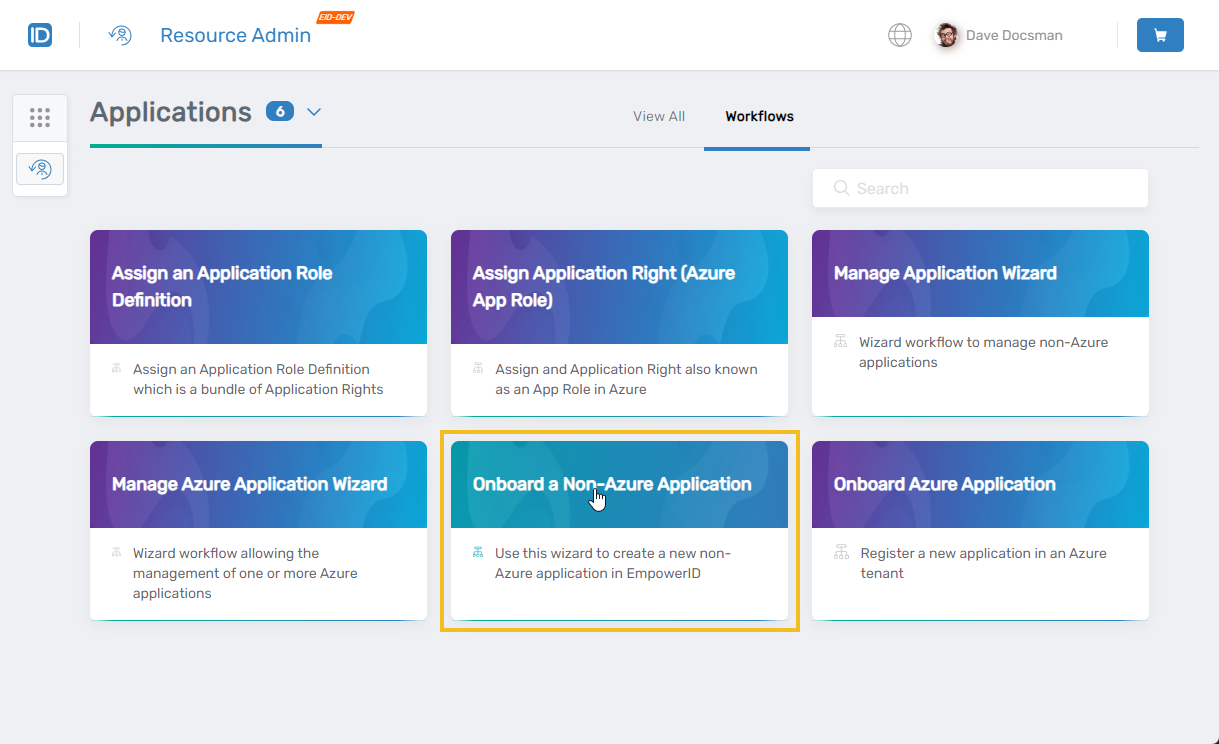
The Onboard Application wizard opens.
 Field Visibility
Field VisibilityThe fields displayed in the workflow may differ based on your workflow parameter configuration.
-
Complete the wizard sections with the appropriate information for your application.
Application Details
Field Description Action Name Name of the application Enter the application name (no spaces or special characters). Display Name User friendly name of the application Enter a display name for the application. Description Brief characterization of the application Enter a description. Select a Location EmpowerID location to be used for RBAC access to the application. Select an EmpowerID location for the application. Select Account Store Inventoried account store (directory) with application resources. In most cases, EmpowerID should be selected. Select the inventoried account store (directory) with the resources the application applies to. PBAC App Specifies whether the application is a PBAC app. When selected, EmpowerID creates a Resource Module for the application. Select this option to specify that the app is a PBAC app. App Authorization Model Defines the framework within the application for managing user access to its data, specifying how permissions are structured and enforced. Select the appropriate app authorization model. For example, if the app does not have any app resources stored in the EmpowerID Identity Warehouse for access control, but does have field types, you would select "PBAC App: No App Resources, Yes Field Types." Allow Shop for Role Definitions Specifies whether users can shop for any role definitions created for the application. Enable/disable the setting for your situation. Allow Shop for Rights Specifes whether users can shop for any rights created for the application. Enable/disable the setting for your situation. Allow Shop for App Management Roles Specifies whether users can shop for any Management Roles created for the applications. Enable/disable the setting for your situation. Owner Information
When onboarding an application, specify the individuals responsible for its management and oversight, including the responsible party, owners, and deputies.
Field Description Action Responsible Party Identifies the primary individual accountable for the application. Enter the name of the person responsible for managing the application (required). Owners Lists the people who have ownership rights over the application. Enter the names of individuals designated as owners, one at a time (optional but recommended). Deputies Specifies secondary contacts or assistants to the owners. Enter the names of individuals assigned as deputies, one at a time (optional). IAM Shop Settings
When making an application requestable in the IAM Shop, configure settings that dictate how requests are handled and who can access them.
Field Description Action Set Requestable Setting Specifies if users can request access to the application in the IAM Shop. Enable to make the application available to eligible users in the IAM Shop; otherwise, disable. Select Access Request Policy Defines the policy to be used for processing application requests. Choose the policy that defines how requests for the application are handled. For applications, the Default policy is suggested—it routes access requests to application owners for approval. Eligible to Request Specifies users allowed to request access to the application. Select the assignee type (Person, Group, Management Role) and identify the individuals, groups, or roles eligible to make requests. Pre-approved for Access Specifies users who are pre-approved for access to the application, bypassing the need for manual request approval. Select the assignee type and identify the individuals, groups, or roles pre-approved for the application. Suggested Assignees Identifies users who will see the application as a suggested resource that they can request. Select the assignee type and identify the individuals, groups, or roles suggested for application access. -
Review the summary information for the application and click Submit.
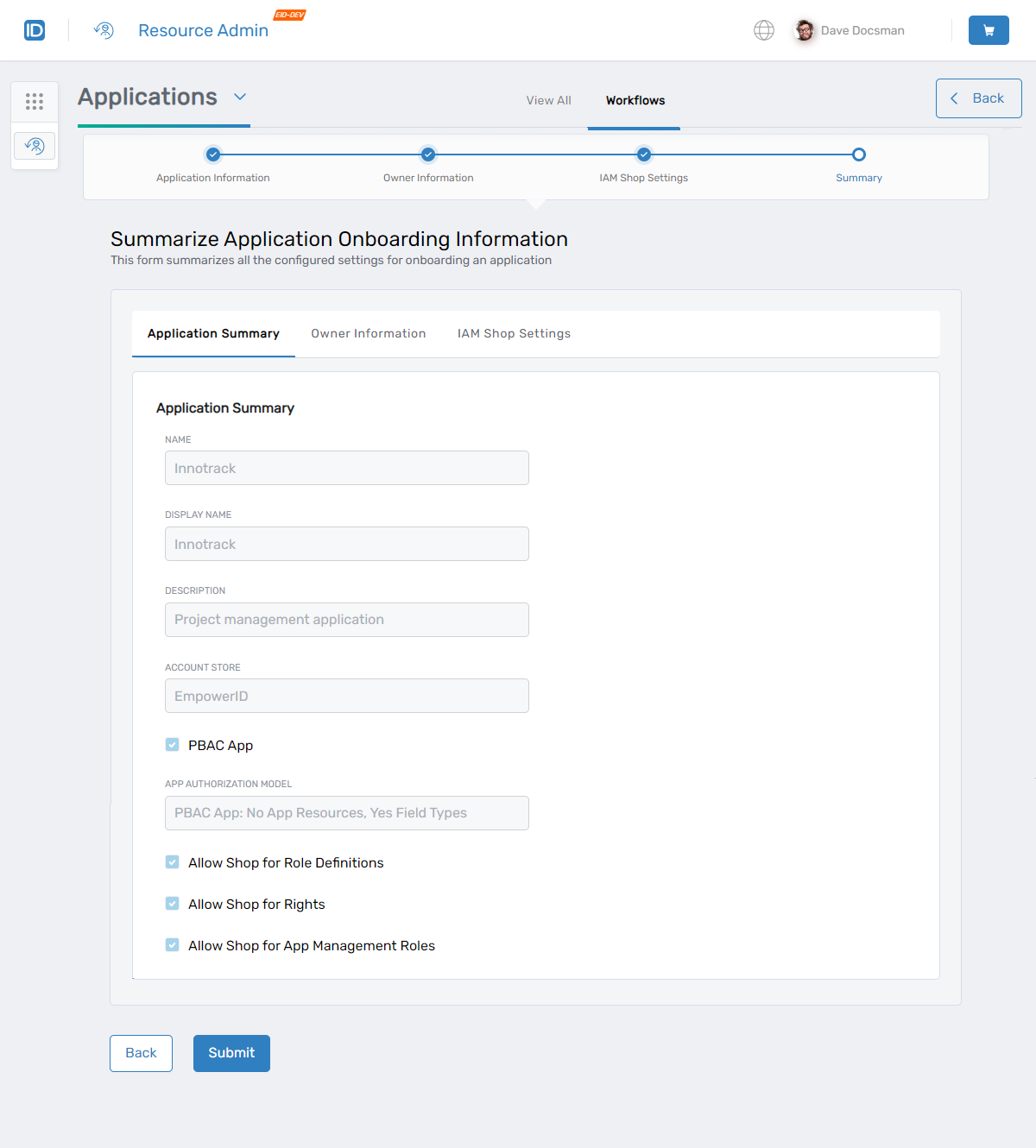
-
Click Submit to close the Operation Execution Summary and exit the wizard.
Verify the Results
To confirm the application was onboarded successfully:
- Locate the application in Resource Admin and click the Details button for the application record.
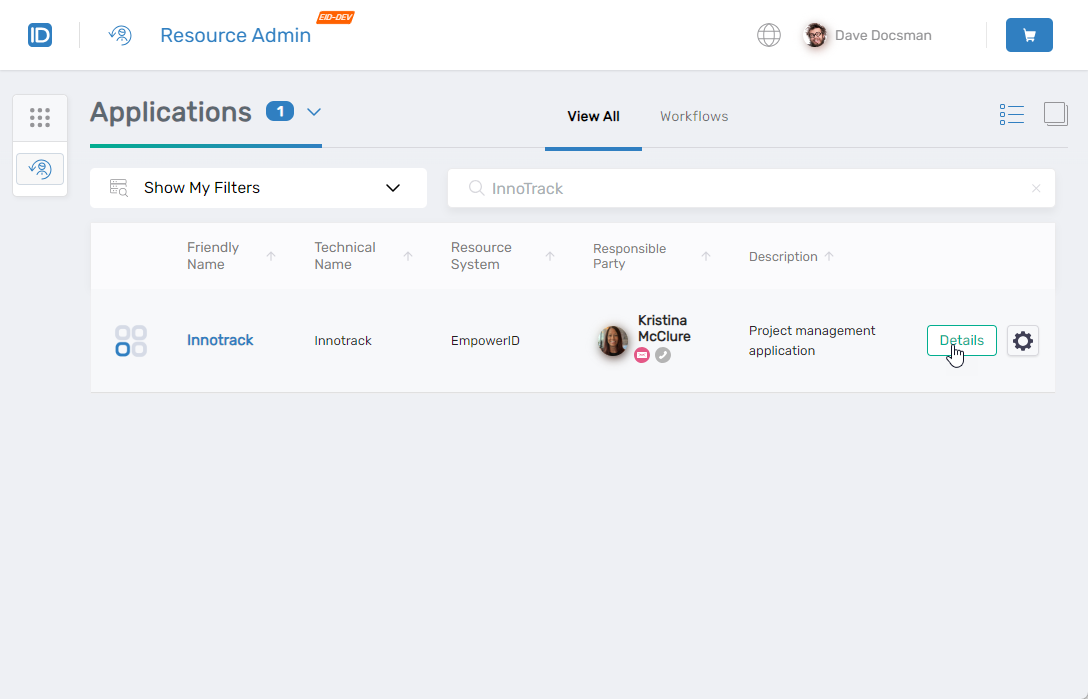
- On the Overview page, verify that the general information and eligibility settings match what was submitted.
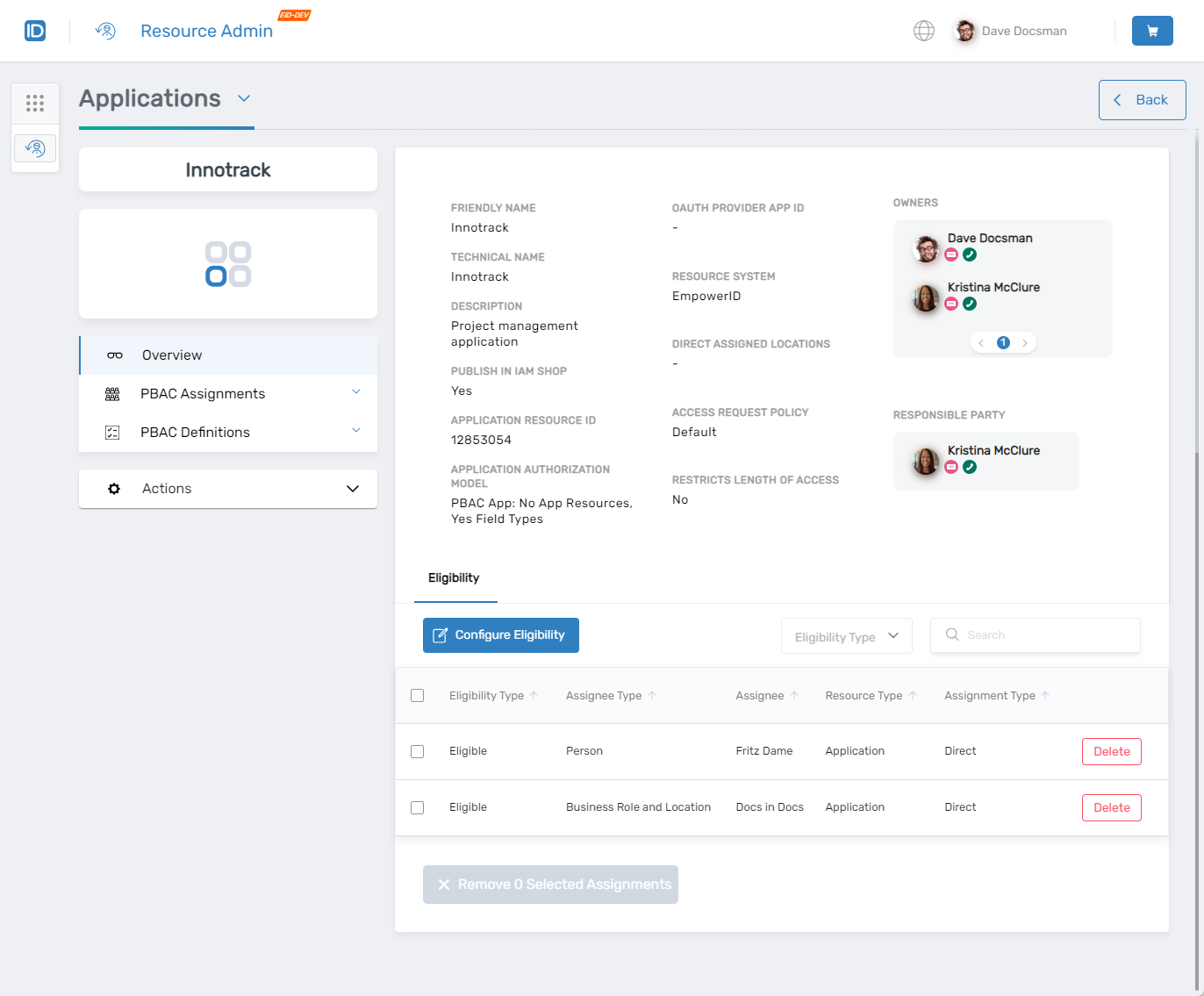
All onboarding actions are logged for audit purposes. The application creator receives temporary "All Access" for two hours to complete initial configuration.
Next Steps
After onboarding your PBAC application:
- Create application-owned field types for fine-grained access control
- Configure application rights users can request
- Set up PBAC policies to enforce access rules
- Test the application request flow in the IAM Shop (if configured as requestable)