EmpowerID Hybrid Access Control (RBAC, ABAC, and PBAC)
Organizations face a fundamental tension in access control: they need the structure and auditability of role-based models while also requiring flexibility for dynamic, context-aware decisions. Role-Based Access Control (RBAC) excels at organizing permissions and modeling organizational hierarchies but struggles with scenarios requiring real-time evaluation of user attributes, resource characteristics, or environmental conditions. Attribute-Based Access Control (ABAC) provides runtime flexibility but can be difficult to audit and manage without underlying structure.
EmpowerID resolves this tension through a hybrid approach integrating both models' strengths. Rather than forcing a choice between RBAC's structure and ABAC's flexibility, EmpowerID's architecture enables them to work together—using RBAC to establish the foundational framework for roles, permissions, and organizational policies, while leveraging ABAC principles to refine decisions based on real-time context.
EmpowerID delivers a comprehensive solution for managing authorization policies by seamlessly integrating RBAC, ABAC, and PBAC. This approach ensures organizations can effectively and dynamically manage access control across various applications and use cases, providing a secure and compliant environment.
The Foundation: RBAC for Structure and Governance
EmpowerID employs RBAC relational modeling to establish a structured framework for an organization's hierarchy, roles, and policies. This framework enables security architects to model organizational structure, including segregation of duties policies preventing undesired access combinations.
RBAC provides critical capabilities forming the foundation of EmpowerID's access control model:
Organizational Modeling - RBAC enables administrators to represent organizational structure through Business Roles and Locations, Management Roles, and relationships between people and resources. This modeling creates a clear, auditable representation of who should have access to what based on position and responsibilities.
Pre-Calculated Permissions - EmpowerID pre-calculates which users have which permissions based on role assignments, group memberships, and location within the organizational hierarchy. These pre-calculated results account for inheritance and attribute-based queries, providing a performance-optimized foundation for access decisions.
Audit and Compliance - RBAC's structured approach enables straightforward answers to questions like "Who has access to this resource?" and "What access does this user have?" Essential for compliance activities, access certifications, and security audits, the static nature of role assignments creates a clear, reviewable audit trail.
Lifecycle Management - When users change roles, transfer departments, or leave the organization, RBAC provides clear mechanisms for updating access. Role-based assignments update systematically, ensuring access changes align with organizational changes.
This RBAC foundation provides the structure necessary for governance at scale. Organizations can define policies, delegate administration, and maintain compliance through well-understood role-based mechanisms proven effective across decades of identity management implementations.
EmpowerID's Three-Tiered RBAC Structure
EmpowerID implements RBAC through a three-tiered model that provides flexibility and granularity while maintaining clear organizational structure:
Tier 1 - Business Roles & Locations: Represents organizational structure combining job function with geography. This tier models how the organization actually works.
Tier 2 - Management Roles: Defines administrative capabilities that can be scoped to specific locations. These roles enable delegated administration across the enterprise.
Tier 3 - Access Levels: Bundles of operations and rights that grant specific capabilities. Access Levels are assigned to roles and can be scoped to control what the role can affect.
This three-tiered structure provides the organizational modeling that RBAC is known for while maintaining the flexibility to adapt to complex enterprise requirements.
Enhancing RBAC with Attribute-Based Assignment
While RBAC traditionally relies on manual role assignments, EmpowerID extends this model by enabling attribute-driven automation of role and group membership. Using attributes such as department, region, or project assignment, administrators define rules automatically assigning users to groups and roles based on current organizational data.
Example: Automated Department Access
Consider an organization with regional finance teams. Without attribute-based automation, administrators must manually add new finance employees to appropriate regional groups, remove employees transferring to other departments, and update access when employees move between regions.
With attribute-based membership policies, the system automatically evaluates user attributes. When Sarah's Department changes to "Finance" and Region to "North America," she's automatically added to the Finance North America group. When she later transfers to Finance EMEA, her region attribute change triggers automatic removal from the NA group and addition to the EMEA group—immediately, without manual intervention.
This automation reduces administrative overhead while maintaining the clear structure and auditability RBAC provides. Administrators can still review who has access and why—the difference is that automated attribute-based rules supplement manual assignments.
The Enhancement: ABAC for Dynamic, Context-Aware Decisions
While RBAC provides essential structure, many access control scenarios require evaluating conditions determinable only at access time. EmpowerID leverages ABAC's flexibility and real-time contextual nature to support centralized decision-making for applications interacting with the EmpowerID API for authorization decisions.
The ABAC engine works hand-in-hand with the robust RBAC engine to enhance or modify its decisions when necessary, considering factors such as risk, location, and MFA type.
ABAC extends EmpowerID's capabilities in several key ways:
Runtime Context Evaluation - ABAC policies evaluate conditions known only at access time. Is the user accessing from a trusted network? Did they authenticate with MFA? Is the system in emergency mode? Is the resource marked confidential? These conditions cannot be pre-calculated and must be evaluated when access is requested.
Fine-Grained Resource Control - While RBAC might grant a user access to "all financial reports," ABAC refines that decision based on specific resource attributes. A user might view financial reports for their department but not others, or view reports marked "internal" but not those marked "confidential." These resource-specific decisions are evaluated dynamically based on resource attributes.
Relationship-Based Authorization - ABAC enables policies considering relationships between users and resources. A manager might access reports about direct reports, or a project member might access project documents. These relationship-based rules are evaluated at access time based on current organizational data.
Environmental Factors - ABAC policies incorporate environmental conditions into authorization decisions. Access might be restricted to business hours, require stronger authentication from external networks, or be denied entirely during system maintenance. These conditions adapt automatically as the environment changes.
The ABAC engine operates as a decision point applications can query for authorization. Rather than embedding authorization logic in each application, applications send relevant attributes about the user, resource, action, and environment to EmpowerID, which evaluates policies and returns an access decision.
ABAC Attribute Evaluation Model
ABAC policies evaluate four types of attributes to make access decisions:
The policy engine evaluates all relevant attributes against policy rules in real-time, enabling context-aware decisions that adapt to current conditions.
Example: Context-Aware HR Access
Consider an HR application that manages sensitive employee data. The hybrid approach enables:
RBAC Layer - HR Managers have a role granting access to view employee records ABAC Layer - Additional conditions refine this access:
- Managers can only view records for their direct reports (relationship attribute)
- Access to salary information requires accessing from the corporate network (environmental attribute)
- Viewing confidential performance reviews requires MFA within the last hour (authentication attribute)
- Emergency access mode allows broader access during critical incidents (system state attribute)
The same HR Manager role behaves differently based on context. From the office on a Tuesday afternoon with MFA, the manager has full access to their team's data. From home on Saturday without MFA, access is restricted. The RBAC role provides the baseline, while ABAC conditions ensure appropriate controls for the specific context.
The Integration: How RBAC and ABAC Work Together
The hybrid model's power lies in how RBAC and ABAC complement each other. Rather than operating independently, they work together in an integrated authorization framework.
RBAC Provides the Base Permissions - When evaluating an access decision, EmpowerID first considers the user's RBAC-based permissions. Does the user have a Management Role granting access to this resource type? Are they assigned to a Business Role and Location providing the necessary Access Levels? Do their group memberships grant relevant rights? These RBAC-based permissions establish the foundation for the access decision.
ABAC Refines Based on Context - Once base permissions are established through RBAC, ABAC policies can enhance or constrain those decisions based on runtime conditions. A user might have RBAC permissions to access a resource, but ABAC policies might deny access because they're connecting from an untrusted network, the resource's sensitivity level exceeds their clearance, or they haven't authenticated with sufficient strength.
Pre-Calculated Results Inform ABAC - Incorporating pre-calculated access results derived from complex RBAC policies bolsters ABAC policy effectiveness. Rather than requiring ABAC policies to re-evaluate complex organizational hierarchies or role inheritances at runtime, EmpowerID leverages pre-calculated RBAC results as inputs to ABAC evaluation. This hybrid approach ensures organizations can effectively manage access control across a wide range of applications and use cases.
Incorporating pre-calculated access results derived from complex RBAC policies, which account for inheritance and attribute-based queries, bolsters the potency of ABAC policies. This hybrid approach ensures organizations can effectively manage access control across a wide range of applications and use cases.
How the Models Work Together
The diagram below illustrates EmpowerID's unique hybrid approach, showing how RBAC's structured 3-tiered role model on the left integrates with ABAC runtime policy evaluation on the right to deliver comprehensive, context-aware access control:
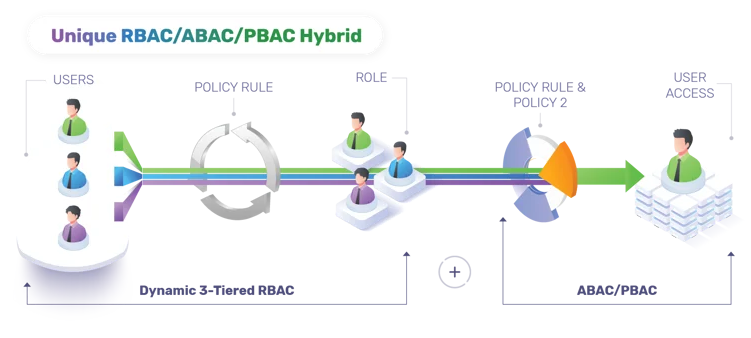 Figure: EmpowerID's hybrid model integrating RBAC's dynamic 3-tiered structure with ABAC runtime policy evaluation
Figure: EmpowerID's hybrid model integrating RBAC's dynamic 3-tiered structure with ABAC runtime policy evaluation
Consider a practical example that demonstrates this integration: A user with the "Department Manager" role (RBAC) requests access to view an employee absence report (resource). The RBAC evaluation confirms that Department Managers have the necessary Access Level to view absence reports. However, the ABAC evaluation then checks additional conditions:
- Is the user the manager of this specific employee? (relationship attribute)
- Is the report marked as confidential? (resource attribute)
- Is the user accessing from the corporate network? (environmental attribute)
- Did the user authenticate with MFA? (authentication attribute)
All conditions must be satisfied for access to be granted. The RBAC role provides the baseline eligibility, while ABAC ensures that the specific context of this access request meets all necessary criteria.
The Hybrid Decision Flow
The following diagram illustrates how RBAC and ABAC evaluations work together to make access decisions:
Key Points:
- RBAC acts as the baseline: Without RBAC permissions, access is denied immediately (efficient pre-calculated check)
- ABAC refines the decision: With RBAC permission, ABAC evaluates runtime conditions for final authorization
- All ABAC conditions must pass: Any failing condition results in denial even with valid RBAC permissions
- Performance optimized: Quick RBAC check first, more expensive ABAC evaluation only when RBAC passes
Implementation Through Policy-Based Access Control
EmpowerID implements this hybrid model through Policy-Based Access Control (PBAC), the practical framework combining RBAC and ABAC capabilities. PBAC is not a separate access control model competing with RBAC or ABAC—it is the implementation mechanism bringing them together in EmpowerID.
PBAC for Membership Automation
EmpowerID uses PBAC Membership Policies to automate RBAC assignments through attribute evaluation. Administrators define policies evaluating user attributes—such as department, region, or project assignment—to automatically assign users to groups and roles.
How Membership Policies Work:
- Field Types define attributes - Administrators create field types representing organizational data (Department, Region, Project, Clearance Level)
- Policies specify conditions - A policy states: "Users with Department = Finance AND Region = EMEA belong to Finance EMEA Team"
- Attributes are assigned to users - Sarah receives Department: Finance and Region: EMEA
- Policies evaluate continuously - The system checks Sarah's attributes against policy conditions
- Membership updates automatically - Sarah is added to Finance EMEA Team; when her attributes change, membership updates accordingly
This automation maintains RBAC structure—groups and roles remain the mechanism for granting access—while reducing manual effort to keep memberships current. Auditors can still see that Sarah belongs to Finance EMEA Team; the difference is this membership is maintained automatically based on her attributes rather than through manual assignment.
PBAC Membership Policy Flow
The following diagram shows how PBAC Membership Policies automate RBAC assignments using attribute evaluation:
How it works: When Sarah's region changes from EMEA to NA, the policy automatically removes her from Finance EMEA Group. A separate policy for Finance NA Group then adds her there, ensuring her access stays aligned with her current role without manual intervention.
PBAC for Application Authorization
For applications requiring runtime attribute evaluation, EmpowerID implements ABAC through PBAC authorization policies. These policies define application-specific rights and evaluate field types at access time to make dynamic authorization decisions.
Application Authorization Progression
Applications can implement progressively sophisticated authorization models based on their requirements:
Choosing the Right Level:
| Level | When to Use | PBAC Features | Security Granularity |
|---|---|---|---|
| Level 1 | Simple internal tools, stable access patterns | None (basic RBAC) | Basic |
| Level 2 | Applications with distinct resources needing individual control | App Resources only | Moderate |
| Level 3 | Context matters (time, location, device, MFA), relationship-based access | Field Types only (ABAC) | High |
| Level 4 | Mission-critical systems, complex compliance, maximum security control | Resources + Field Types | Very High |
Field Types: The Common Attribute Layer
Field Types provide a unified attribute layer used across both RBAC automation and ABAC evaluation:
Key Insight: Field Types are defined once and used in multiple contexts. The same "Department" field type can:
- Determine automatic group membership (RBAC automation through PBAC Membership Policies)
- Control application access decisions (ABAC implementation through PBAC Authorization)
This unified attribute layer ensures consistency—"Department: Finance" means the same thing whether it's used for membership or authorization.
Assignment Points: Precise Permission Scoping
Assignment Points define the exact locations or entities within a system where permissions apply. Rather than granting broad access across an entire application or tenant, Assignment Points enable precise scoping that prevents over-provisioning.
For example, in Microsoft Entra ID environments, Assignment Point Types correspond to Azure's resource hierarchy:
- Tenant Root - Rights applied globally across the entire tenant
- Management Group - Rights scoped to specific management groups
- Subscription - Assignments at the subscription level
- Resource Group - Rights limited to specific resource groups
An administrator might assign a user the "Contributor" role at the Subscription level, granting permissions within that specific subscription while preventing access at the tenant level or to other subscriptions. This hierarchical scoping ensures that permissions are granted only where needed.
Different systems implement Assignment Points according to their architecture. SAP systems use organizational attributes like company code or plant. Custom applications define their own logical hierarchy. This flexibility allows Assignment Points to adapt to different system structures while maintaining precise permission control.
Projection: Extending the Hybrid Model to External Systems
Many organizations need to enforce hybrid access policies in external systems that don't natively support ABAC or sophisticated policy evaluation. EmpowerID addresses this through Projection, which extends policies to external systems while maintaining centralized policy management.
How Projection Works:
External groups are designated as Fulfillment Groups and mapped to specific rights or roles in EmpowerID. When policies grant or revoke rights, the projection engine evaluates whether users should be added to or removed from the corresponding Fulfillment Groups in the external system. This synchronization happens automatically, ensuring that access control remains consistent.
Example: Azure AD Projection
A policy grants the "Contributor" role to Finance department users for the North America subscription, with conditions requiring MFA authentication. The Contributor role is mapped to an Azure AD group that grants actual permissions in Azure. When users satisfy the policy conditions, EmpowerID adds them to the Azure AD group automatically. If conditions are no longer met—such as a user transferring out of Finance—EmpowerID removes them from the group.
This approach enables organizations to leverage the hybrid model's dynamic, attribute-based policies even when working with systems that only understand traditional group-based permissions. It provides centralized governance while respecting the native authorization models of diverse systems.
PBAC Policy Structure
PBAC policies bring RBAC and ABAC elements together in a structured, manageable format. Each policy:
- Grants a single right or role (RBAC element) - Clear about what capability is being assigned
- To a specific assignee (RBAC actor) - Person, group, Business Role and Location, Management Role, or query-based collection
- May include field type conditions (ABAC element) - Attribute-based conditions evaluated at runtime
- May be scoped to specific resources or locations (RBAC scoping) - Limits where the granted right can be exercised
This structure ensures that each policy has a clear purpose and can be understood independently. When multiple policies apply to a request, EmpowerID evaluates all relevant policies and their conditions to determine the final authorization decision.
Choosing Your Approach: When to Use RBAC Alone or Add PBAC Capabilities
Understanding when to enhance RBAC with PBAC capabilities is essential for effective access control design. In EmpowerID, RBAC is always the foundation—the question is whether to add PBAC Membership Policies, PBAC Authorization, or both.
Use RBAC Alone When:
- Permissions align clearly with roles and access needs match organizational job functions
- Manual assignments are manageable due to small user population or infrequent changes
- Audit requirements favor simplicity with clear, static assignments for easy certification
- Administrative resources are limited and team prefers straightforward role and group management
- No runtime context is needed and access decisions don't depend on time, location, or other dynamic factors
Example: An internal HR system where HR Generalists, HR Managers, and HR Directors have distinct permissions that rarely change. Basic RBAC with manual role assignments provides sufficient control.
Add PBAC Membership Policies When:
- Organizational attributes drive access and department, location, or project assignment determines group membership
- User population changes frequently with common new hires, transfers, and departures
- Manual assignment overhead is high and administrators spend significant time updating group memberships
- Audit trails should include "why" and show membership based on documented rules, not manual decisions
- Consistency across regions is important and same rules should apply regardless of local administrator preferences
Example: A global enterprise where employees automatically join regional and departmental groups based on HR attributes. When someone transfers from Finance in London to Finance in New York, group memberships update automatically without IT intervention.
Add PBAC Authorization When:
- Context determines access and time, location, device, or authentication method matters
- Fine-grained resource control is needed with different users needing different access to the same resource type based on attributes
- Relationship-based access is required for managers accessing direct report data or project members accessing project resources
- Environmental factors are critical and network location, system state, or risk scores affect decisions
- Application-specific scoping is needed where users can access some categories/regions but not others
Example: A financial reporting application where Regional Finance Managers can view reports from their region during business hours from the corporate network, but require additional approval for after-hours access or when working remotely. The same RBAC role behaves differently based on runtime context.
Use Both PBAC Capabilities When:
- You need automation and runtime control to both automate RBAC assignments AND evaluate runtime conditions
- Different applications have different needs where some require automated membership, others need context-aware authorization
- Compliance and agility are both priorities requiring auditable attribute-based rules with dynamic context evaluation
- Enterprise-wide consistency is critical using the same attribute layer for both membership and authorization
- Centralized policy management is important for consistent decisions across diverse applications and use cases
Example: An enterprise where PBAC Membership Policies automatically maintain department and regional group assignments, while PBAC Authorization evaluates runtime conditions for sensitive applications like financial systems, requiring both organizational structure (RBAC) and context-aware decisions (ABAC principles).
Decision Framework: Choosing Your Access Control Approach
Use this decision framework to determine which PBAC capabilities to add to your RBAC foundation:
Quick Decision Guide:
| If You Need... | Then Use... |
|---|---|
| Simple role-based access, manual OK | RBAC Only |
| Auto-update groups on dept/region change | RBAC + PBAC Membership |
| Context-aware access (time, location, MFA) | RBAC + PBAC Authorization (Level 3) |
| Maximum control (resources + context) | RBAC + PBAC Membership + Authorization (Level 4) |
Remember: RBAC is always the foundation in EmpowerID. PBAC capabilities are optional enhancements you add based on specific requirements.
Implementation Considerations for Administrators
Successfully implementing the hybrid approach requires understanding several practical considerations:
Start Simple, Add Complexity Gradually
Begin with RBAC for most applications and add PBAC capabilities where specific requirements demand them. This approach reduces the initial learning curve for administrators, allows teams to build expertise progressively, avoids over-engineering access control for simple applications, and makes troubleshooting easier during early adoption.
Attribute Infrastructure is Critical
Both attribute-based membership and application authorization depend on accurate, available attribute data. Consider: Where will attributes come from (HR systems, directories, manual entry)? How often do attributes need to refresh? Can attribute lookups support required response times? Are attributes accurate and consistently maintained?
Invest in attribute infrastructure before implementing sophisticated policies that depend on it.
Balance Performance with Flexibility
The hybrid approach balances pre-calculated RBAC results with runtime ABAC evaluation. Optimize by using RBAC for stable, frequently-evaluated permissions; caching attribute values that don't change often; pre-calculating complex organizational hierarchies; and reserving runtime ABAC evaluation for truly dynamic conditions.
Monitor performance as you add ABAC policies to ensure acceptable response times.
Policy Testing and Validation
Complex policies combining RBAC and ABAC require thorough testing. Test policies in development environments before production, use policy simulation tools to understand who will have access, validate that policies work correctly across all attribute combinations, monitor policy behavior in production to detect unintended results, and document policy intent for future administrators.
Common Implementation Mistakes
Avoid these frequent pitfalls:
Over-complicated policies - Adding ABAC conditions that could be handled through simpler RBAC scoping. Start simple and add complexity only when justified.
Insufficient attribute data - Building policies that depend on attributes that aren't reliably available or current. Ensure data infrastructure before policy implementation.
Neglecting audit requirements - Creating policies that are difficult to explain during audits. Document policy logic clearly and maintain audit trails.
Inconsistent field type usage - Using different attributes for similar purposes across applications. Standardize field types for consistency.
Poor change management - Modifying policies without understanding downstream impacts. Test changes thoroughly and communicate with stakeholders.
Establishing Governance
Effective hybrid access control requires clear governance: Define who can create policies (not all administrators should manage ABAC policies); document policy standards establishing conventions for naming, structure, and documentation; conduct regular policy reviews periodically validating that policies still reflect intended access patterns; implement change approval processes requiring review before policy modifications reach production; and maintain audit trails ensuring all policy changes and access decisions are logged.
Benefits of the Hybrid Approach
The hybrid model, implemented through PBAC's enhancement of RBAC with ABAC principles, provides several advantages:
Governance and Flexibility - Organizations maintain RBAC's clear governance model—roles, delegations, and access certifications work as they always have—while gaining the ability to make nuanced, context-aware decisions through PBAC Authorization when needed. Security policies can be both structured and adaptive.
Performance and Scalability - By pre-calculating RBAC-based permissions and using those results as inputs to ABAC evaluation in PBAC policies, EmpowerID avoids the performance penalty of evaluating complex organizational hierarchies at every access decision. The system scales efficiently while maintaining comprehensive control.
Auditability with Context - Access decisions remain auditable because they're based on both explicit role assignments (enumerable and reviewable) and documented PBAC policies (specifying evaluated conditions). Auditors can understand both who was granted access through RBAC and what conditions were checked through PBAC Authorization.
Reduced Complexity - Organizations don't need to express everything through roles (leading to role explosion) or through complex dynamic policies (difficult to understand and maintain). They can use RBAC for stable, role-based permissions and add PBAC capabilities—membership automation or application authorization—only where needed.
Consistent Enforcement - Applications integrating with EmpowerID's PBAC Authorization API receive consistent access decisions considering both organizational policies (RBAC) and runtime context (ABAC principles). This consistency ensures security policies are enforced uniformly across diverse applications and systems.
Progressive Adoption - Organizations can start with RBAC-only implementations and progressively add PBAC Membership Policies for automation and PBAC Authorization for context-aware application access as requirements evolve. This reduces the learning curve and allows teams to build expertise gradually while delivering immediate value.
Summary
EmpowerID unites RBAC and ABAC through its Policy-Based Access Control (PBAC) implementation to offer a comprehensive solution for managing authorization policies. This hybrid method provides the necessary structure for governance and compliance through RBAC, while adding flexibility for context-aware decisions through ABAC principles implemented via PBAC.
The hybrid approach recognizes that RBAC provides the essential foundation for all access control in EmpowerID. Organizations build on this foundation by adding PBAC capabilities where needed:
PBAC Membership Policies enhance RBAC by automating group and role assignments based on user attributes, reducing administrative overhead while maintaining clear structure and auditability.
PBAC Authorization implements ABAC principles for applications requiring runtime evaluation of context and attributes, adding dynamic, context-aware decision-making on top of the RBAC baseline.
By layering these capabilities, EmpowerID enables organizations to implement sophisticated access control policies impractical with RBAC alone, while maintaining the governance structure pure ABAC implementations often lack. Organizations can start with RBAC and progressively adopt PBAC capabilities—membership automation, application authorization, or both—as requirements evolve, ensuring access control keeps pace with business needs while maintaining the governance and auditability compliance demands.