What is Attribute-Based Access Control?
Attribute-Based Access Control (ABAC) is a policy-based access control model that grants or denies access to resources based on attributes associated with the subject (user), object (resource), action, and environment. Unlike traditional access control models that rely on predefined roles and static permissions, ABAC evaluates these decisions dynamically at runtime using a set of policies defined over those attributes.
According to the NIST SP 800-162 definition:
"An access control method where subject requests to perform operations on objects are granted or denied based on assigned attributes of the subject, assigned attributes of the object, environment conditions, and a set of policies that are specified in terms of those attributes and conditions."

Figure 1: NIST SP 800-162 ABAC Definition
This approach represents a fundamental shift from how organizations traditionally think about access control. Rather than asking "Does this user have the right role?", ABAC asks "Do this user's attributes, this resource's attributes, the requested action, and the current environment satisfy the access policy?" This shift enables more precise and adaptive access control, but it also introduces new complexities that organizations must understand before adoption.
The Fundamental Difference from RBAC
To understand ABAC's value, it's helpful to contrast it with Role-Based Access Control (RBAC), the predominant model in most organizations. RBAC assigns users to roles, and roles are granted permissions to resources. A user's access is determined by their role membership, which is typically static until explicitly changed by an administrator.
Consider a simple example: In an RBAC model, Alice might be assigned to a "Manager" role, and that role is granted permission to view all employee absence reports. This is straightforward and easy to administer, but it's also inflexible. Alice can view absence reports for employees she doesn't manage, and she retains this access even when working from untrusted networks or when the reports contain highly sensitive information.
ABAC approaches this differently. Instead of granting access based solely on role membership, an ABAC policy might state: "A user can view an employee's absence report if the user is the employee's manager, the user is accessing from the corporate network, the user authenticated with MFA, and the report is not marked confidential." This policy considers the relationship between Alice and the specific employee, the context of the access request, and the sensitivity of the resource itself.
The power of this approach becomes evident in complex scenarios. Without ABAC, an organization trying to enforce these conditions through RBAC would need to create numerous roles to cover all combinations: "ManagerFromCorporateNetwork", "ManagerWithMFA", "ManagerForNonConfidentialReports", and so on. This leads to role explosion—a proliferation of highly specific roles that become difficult to manage and understand. ABAC avoids this by evaluating conditions dynamically rather than encoding them in static role assignments.
How ABAC Evaluates Access
ABAC policies make authorization decisions by evaluating four types of attributes. Subject attributes describe the user or entity making the request, such as their department, job title, clearance level, certifications, or relationships with other users. Resource attributes describe what is being accessed—its sensitivity level, owner, creation date, department association, or data classification. Action attributes specify the operation being requested, whether viewing, updating, deleting, exporting, or approving. Environment attributes capture the context of the request: the time of day, network location, IP address, system state, or authentication method used.
Because these attributes are evaluated at runtime, ABAC policies can incorporate dynamic and contextual data that would be impossible to pre-compute in a static model. A policy can check whether a user's MFA token was issued within the last hour, whether the request originates from a specific geographic region, or whether the system is currently in emergency mode—all factors that may change moment to moment.
This runtime evaluation is both ABAC's greatest strength and one of its primary challenges. It enables incredibly flexible and context-aware access control, but it also means that policy decisions depend on the availability and accuracy of attribute data at the moment of the access request. If an attribute source is unavailable or returns stale data, policy evaluation may fail or produce incorrect results.
A Real-World Example: Medical Records Access
To illustrate ABAC's capabilities, consider a real policy implemented in an EmpowerID demonstration. In this scenario, Alice requests access to view Bob's X-Ray image. Rather than simply checking whether Alice has a "Doctor" role, the policy evaluates multiple conditions simultaneously.
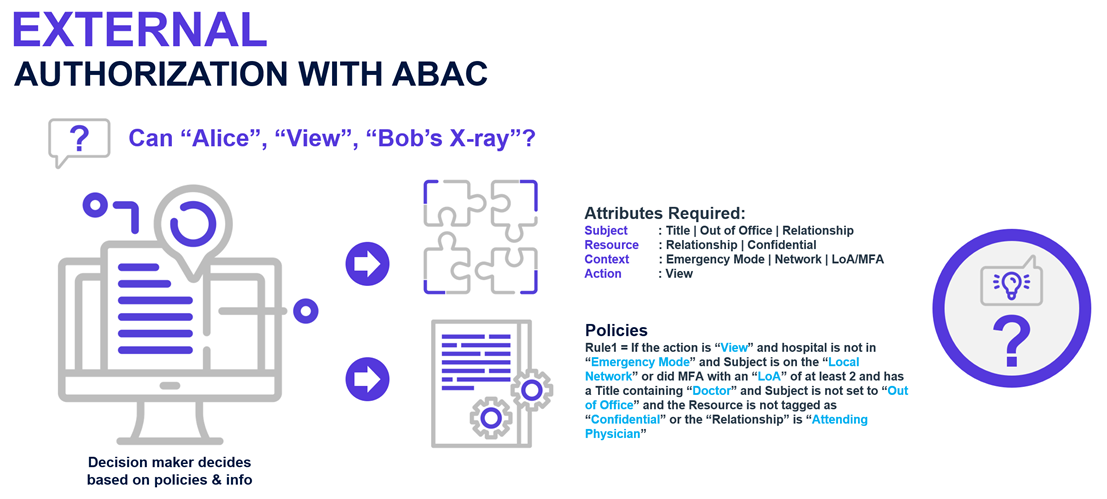
Figure 2: Elaborate ABAC policy showing the potential of ABAC
The policy first checks that the requested action is "View" rather than "Edit" or "Delete." It then verifies that the organization is not in Emergency Mode, which would normally restrict access to patient records to prevent unauthorized viewing during crises. The policy ensures the request comes from the Local Network, confirming Alice is accessing from within the hospital rather than remotely. It checks that Alice authenticated using MFA with a Level of Assurance (LOA) of 2 or higher, ensuring strong authentication.
The policy then examines Alice's role and status, confirming she is in the Doctors role and not marked as Out of Office. It reviews the X-Ray itself to ensure it is not marked Confidential, which would require additional clearances. Finally, it validates the critical relationship: that Alice is Bob's Attending Physician, not just any doctor in the system.
All seven conditions must be satisfied for access to be granted. If Bob's X-Ray were marked Confidential, access would be denied even though Alice is his doctor. If Alice were accessing from home without the VPN connection, the Local Network check would fail. If she had marked herself Out of Office in the system, the policy would deny access to protect patient privacy when the doctor is not actively working.
This scenario demonstrates how ABAC can enforce highly granular and context-sensitive rules that would be difficult or impossible to model using RBAC alone. To achieve equivalent control with RBAC, you would need dozens of roles covering every combination of network location, authentication strength, resource sensitivity, and doctor-patient relationships. The policy maintenance burden would be enormous, and the role structure would be nearly incomprehensible to auditors and administrators.
When ABAC Provides Value
ABAC becomes valuable when authorization rules involve relationships between users and resources—managers viewing reports for their direct reports, or authors editing their own documents. RBAC struggles to express these relationships without creating an explosion of roles for each scenario. ABAC naturally models these through attribute evaluation.
Organizations needing dynamic, context-sensitive policies also benefit from ABAC. When authorization decisions should vary based on time of day, network location, authentication strength, or system state, ABAC evaluates these conditions at runtime. RBAC can approximate some controls through separate systems, but these become complex to manage and often operate independently rather than as unified authorization decisions.
ABAC can address role proliferation. When RBAC implementations grow to hundreds or thousands of roles—many highly specific combinations created for particular scenarios—ABAC often expresses the same policies more concisely through attribute-based rules. This doesn't eliminate all roles, and most organizations find hybrid approaches work best, but it can significantly reduce the role footprint.
Fine-grained access control requirements also point toward ABAC. Rather than creating roles for "Can view Project A documents" and "Can view Project B documents," an ABAC policy can state "Users can view documents for projects they are assigned to," with the system evaluating project membership at access time. Organizations implementing centralized authorization across multiple applications often turn to ABAC to maintain policies in one place rather than scattered across codebases.
The Benefits of Attribute-Based Authorization��
The primary advantage of ABAC lies in decoupling authorization logic from application code. In traditional applications, access control decisions are often hardcoded: "if user.role == 'Manager' then show_absence_reports()". This embeds business logic in application code, requiring code modifications, testing, and deployments for policy changes. ABAC externalizes this logic into policies that can be updated independently of applications, reducing the time and risk associated with authorization changes.
This externalization enables consistency across applications. Rather than each application implementing its own interpretation of business rules, all applications query the same policy decision point and receive consistent answers. This is particularly valuable in organizations with diverse technology stacks where maintaining consistent authorization logic across Java, .NET, and JavaScript applications would otherwise require parallel policy implementations.
ABAC's flexibility comes from operating on attribute values rather than static groupings. Policies can evaluate current conditions—whether a user is working remotely, their current authentication level, whether the system is in emergency mode—without requiring these conditions to be pre-computed and stored as role assignments. This real-time evaluation enables policies to adapt automatically to changing circumstances.
The granularity ABAC provides can reduce administrative overhead when properly implemented. Instead of managing group memberships for every combination of access needs, administrators manage the attributes that policies evaluate. When a new employee joins as a manager in the Engineering department, assigning these attributes automatically grants appropriate access according to policies without requiring membership in dozens of specific access groups.
ABAC policies can also be more transparent to non-technical stakeholders. A policy that references "department," "manager relationship," and "project assignment" speaks in business terms that stakeholders understand, making policy validation more straightforward than RBAC role names, which often become technical identifiers whose meaning requires institutional knowledge.
Implementation Challenges
While ABAC offers significant advantages, successful implementation requires addressing several substantial challenges. The first and often most significant is ensuring attribute data is available with acceptable performance. ABAC policies may need to evaluate attributes from multiple systems—identity stores, HR databases, resource repositories, authentication systems, and network infrastructure. Each attribute lookup adds latency to the authorization decision.
Consider a policy that checks a user's department, their project assignments, the resource classification, and their current network location. If each attribute requires a separate API call to different systems averaging 100 milliseconds, the authorization decision takes at least 400 milliseconds before policy evaluation begins. For interactive applications, this latency may be unacceptable.
Organizations implementing ABAC must carefully design their attribute infrastructure. Some attributes can be cached—a user's department likely doesn't change hourly—while others must be evaluated in real-time, such as network location. Balancing accuracy with performance requires thoughtful analysis of which attributes are needed, how frequently they change, and what staleness can be tolerated. In some cases, pre-computation strategies may be necessary, creating a hybrid between pure ABAC and traditional permission storage.
The second major challenge is policy authoring. Creating effective ABAC policies requires both technical expertise and deep business knowledge. Policy authors must understand the technical policy language and evaluation model, the business rules being expressed, the attributes available and their semantics, and the security implications of policy logic.
While ABAC policies can be expressed in business-friendly terms, authoring policies that are both correct and performant requires specialized expertise. Organizations should plan for training, documentation, and potentially policy authoring tools to support policy creators.
This combination of skills can be difficult to find, especially in organizations new to centralized policy enforcement. Successful ABAC implementations typically require close collaboration between security, business, and technical teams, along with investment in training and potentially specialized policy authoring tools.
Policy management complexity grows as ABAC implementations mature. The flexibility that makes ABAC powerful can lead to policy sprawl if not carefully managed. Without discipline, organizations may accumulate hundreds or thousands of specific rules that become difficult to maintain. Multiple policies may apply to the same access request and reach different conclusions, requiring clear rules for how conflicts are resolved. Testing and validation present another challenge—validating that policies work correctly across all possible attribute combinations is difficult. Organizations need strategies for testing policies before deployment and monitoring policy behavior in production to detect unintended results.
Auditing Challenges
One of the most frequent concerns about ABAC is the complexity it introduces to auditing and compliance activities. In RBAC environments, auditors can ask straightforward questions: "Which roles grant access to this resource?" and "Which users have this role?" The answers are derived from static assignments that can be queried and reported.
ABAC makes these questions more complex because access depends on current attribute values rather than static assignments. When an auditor asks "Who has access to the financial reports?", the answer in an ABAC environment is "Anyone whose attributes satisfy the financial report access policy." This requires evaluating the policy against current user attributes, and the answer may change based on time, location, or other contextual factors. Someone who has access when working from the office may not have access when working from home. Someone who has access during normal business hours may not have access on weekends.

Figure 4: A Common Standard Auditor's Question
Understanding why access was granted or denied requires policy analysis. When investigating an access event, you must trace which policy rules evaluated to true, what attribute values were used in the evaluation, and how those attributes were obtained. This requires comprehensive audit logging that captures not just the policy decision but also the attribute values and the policy evaluation path. Without this level of detail, explaining access decisions to auditors becomes difficult.
Changes to attribute values can affect access without explicit permission changes. If a policy grants access to "all members of the Engineering department," adding someone to the Engineering department (an HR data change) grants them access through the policy. This is powerful but can make it harder to track why someone gained access—the permission system wasn't changed, but an attribute that the permission system evaluates was changed. Organizations need to correlate attribute changes with their access policy implications, which requires understanding which policies reference which attributes.
To address these challenges, organizations implementing ABAC should invest in comprehensive audit logging that captures policy decisions and attribute values at the time of each access decision. Policy analysis tools that can simulate access decisions—"Who would have access to this resource if we deployed this policy change?"—help with both testing and auditing. Clear documentation of policies and their intent makes it possible for auditors who aren't policy experts to understand what rules are being enforced. Regular policy reviews and access certification processes help ensure that policies continue to reflect intended access patterns.
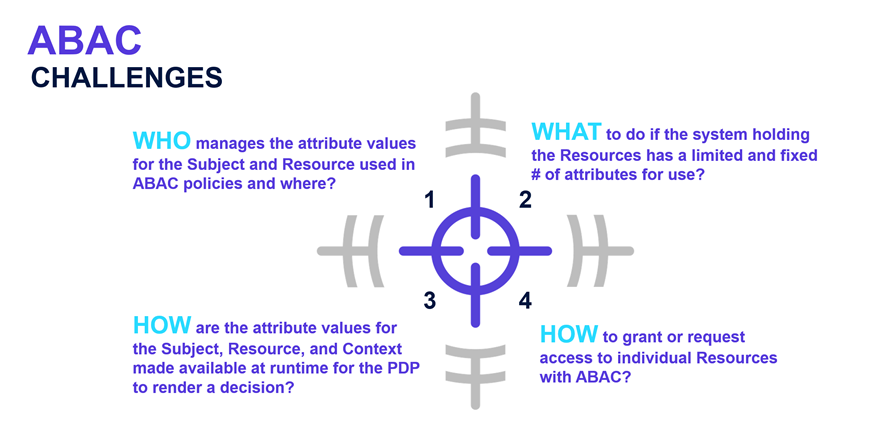
Figure 5: The Who, What, and How of ABAC Challenges
Understanding the Trade-offs
ABAC is not a universal solution, and organizations should understand its trade-offs before adopting it. ABAC excels at expressing complex, context-sensitive authorization rules that would be impractical with traditional approaches. It enables centralized policy management and can reduce role proliferation in complex environments. When properly implemented, it provides flexibility and adaptability that static models cannot match.
However, ABAC is more complex to implement and operate than RBAC. It requires a mature attribute infrastructure where necessary data is available with acceptable performance. Policy authoring requires specialized skills combining technical and business knowledge. Auditing and access review become more complex because access is determined dynamically rather than through static assignments. Performance depends on attribute retrieval speed, which may require careful optimization. Understanding who has access requires policy simulation rather than simple database queries.
Organizations should consider whether ABAC is appropriate for their needs. If authorization requirements are simple and stable, if IT resources and expertise are limited, if attribute data is not readily available or reliable, if application response time requirements are very strict, or if auditors require simple static access assignments, ABAC may introduce more complexity than it solves. Many organizations find that a hybrid approach—using RBAC for straightforward, stable permissions and ABAC for complex, context-sensitive decisions—provides the right balance.
ABAC represents a significant evolution in access control, moving from static role assignments to dynamic, context-aware authorization. It is most effective when used appropriately and often works best in combination with other access control models. Organizations that invest in the necessary infrastructure, expertise, and governance processes can leverage ABAC to enforce sophisticated authorization policies that would be impractical with traditional approaches.
For information on how different access control models can be integrated to leverage the strengths of each approach, see EmpowerID Hybrid Access Control (RBAC, ABAC, and PBAC).