Master Passwords in EmpowerID
EmpowerID's master password system is a core security mechanism that protects sensitive user data through encryption. It is foundational to secure features such as Privileged Access Management (PAM), secrets management, and credential checkout.
This article provides an overview of how the master password system works—covering how users create cryptographic key pairs, how encrypted data is secured and accessed, and what administrative guarantees are in place to prevent unauthorized decryption.
The master password cannot be the same as the user's EmpowerID login password. This separation enhances security by ensuring that if one password is compromised, the other remains secure.
How the Master Password System Works
At its core, the master password system uses asymmetric encryption to ensure that only individual users can decrypt the sensitive data they interact with. This is achieved by generating a unique public/private key pair for each user. The private key is encrypted using the user’s master password, ensuring that even EmpowerID administrators cannot access the user’s secrets without that password.
The system operates across three key stages:
- Initial Setup – Users generate their master password and key pair.
- Data Protection – Data is encrypted using the user’s public key.
- Data Access – Only users with the master password can decrypt the data.
Each stage is explained in detail below.
Initial Setup
When a user first uses a secure feature in EmpowerID—such as checking out a privileged credential or storing a secret—they are prompted to create a master password. This master password is used to protect their cryptographic identity in the system.
Once the password is created, EmpowerID automatically generates a public and private key pair that is uniquely linked to the user. The public key is used to encrypt data. The private key, required for decryption, is encrypted using the master password and stored securely.
If users forget their master password, they can create a new one. However, this process generates a new key pair, and any data encrypted with the original private key cannot be recovered.
To decrypt data later, users must supply their master password to unlock their private key. Without this, decryption is impossible—even for system administrators.
Data Protection
Once a user's key pair is established, EmpowerID uses it to secure sensitive data through public key encryption. This ensures that data is protected from the moment it is created.
- Encryption Process: All sensitive content—such as passwords, credentials, or API keys—is encrypted using the user’s public key.
- Secure Storage: Encrypted data is stored in the EmpowerID platform. Even if someone gains access to the storage layer, the encrypted data cannot be decrypted without the corresponding private key.
- One-Way Encryption: Only the private key can decrypt the data. The public key is used solely for encryption.
This structure ensures that encrypted data is never accessible unless the user unlocks their private key with the correct master password.
Data Access
To view or use encrypted data, the user must authenticate by entering their master password. This password decrypts their private key, enabling the system to perform decryption securely.
- The user’s private key is unlocked only when the correct master password is provided.
- Once unlocked, the private key is used to decrypt previously encrypted data.
- EmpowerID enforces strict access controls: only the user can perform this operation. Even privileged accounts cannot bypass this process.
This approach ensures that sensitive information remains user-controlled and inaccessible to unauthorized parties—even those with administrative access to the system.
Encryption Architecture Overview
The following diagram illustrates the master password system flow:
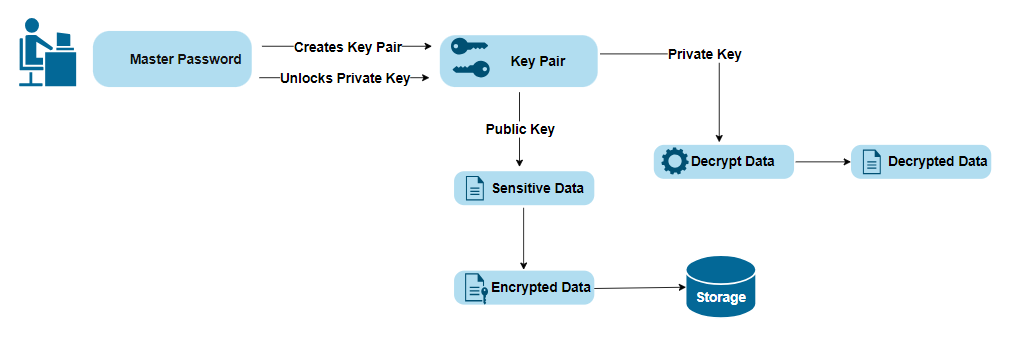
Key Flow Highlights:
- Users create a master password, which is used to protect their private key.
- The system generates a public/private key pair per user.
- The public key encrypts sensitive data for secure storage.
- To decrypt, the user must provide their master password to unlock the private key.
- Only with the private key can data be decrypted—ensuring exclusive access.
User Capabilities with Master Passwords
Users interact with the master password system when they perform operations that involve encryption or access to sensitive data. These operations include creating/viewing passwords, managing secrets, and checking out credentials.
Creating and Viewing Passwords
When users create passwords or secrets in EmpowerID, the system encrypts this information using their public key. This ensures that even during storage or transit, the data remains protected.
To view this data later, users must:
- Provide their master password
- Unlock their private key
- Allow EmpowerID to decrypt the data using the private key
Only users who can complete this process have access to the plaintext version of the password or secret.
Managing Secrets
Secrets such as API tokens, SSH keys, or database credentials are encrypted using the same public key mechanism. This guarantees that the data is secured before being written to storage.
To modify or access these secrets:
- Users must authenticate with their master password
- The private key is unlocked for decryption
- EmpowerID performs the operation securely, limiting access only to the authenticated user
Even if the encrypted data is exposed at the database level, it cannot be decrypted without both the private key and the corresponding master password.
Credential Checkout
The master password system also protects privileged account credentials during checkout.
When a user checks out credentials:
- The credentials are encrypted using the user’s public key
- Decryption requires the user to:
- Enter their master password
- Unlock their private key
- Allow the system to decrypt the credentials
Even if another administrator tries to view the credentials, they will not be able to decrypt them unless they are the original user and possess the correct master password. This upholds least privilege access and ensures non-repudiation in sensitive operations.
Security and Compliance Considerations
The master password system provides strong cryptographic boundaries around user-controlled secrets and credentials. Key points include:
- Zero Trust Enforcement: No decrypted data is stored or accessible without explicit user authentication.
- Auditability: All master password and encryption actions are logged.
- Irrecoverability by Design: Forgotten master passwords result in loss of encrypted data tied to the old key.
- Administrative Isolation: Even system-level accounts cannot access a user’s decrypted secrets without the master password.
This model aligns with best practices in IGA, PAM, and compliance standards by ensuring user autonomy and minimizing insider risk.
Summary
EmpowerID’s master password system protects sensitive user data using asymmetric encryption, secured by a user-defined master password. From key generation and encryption to decryption and access control, the system ensures that only the data owner can view or interact with encrypted content.
This approach enforces strict separation of duties, prevents unauthorized access—even from administrators—and provides a cryptographically sound foundation for secret and credential management in enterprise environments.