Understanding Functions in EmpowerID
Understanding Functions in EmpowerID
In EmpowerID, Functions are used to represent business-level actions that correspond to technical entitlements across systems. They provide an abstraction layer that helps organizations manage and review access more effectively by focusing on what users can do rather than on complex permission strings. Functions play a central role in risk management by enabling clear policies and visibility into user capabilities.
This article explains the types of Functions in EmpowerID, how they are mapped to entitlements, and how they are used in risk analysis.
What Are Functions?
A Function in EmpowerID is a business-defined activity that a person can perform within one or more applications. For example, an SAP entitlement like TCode ME21N may be mapped to a more understandable Function such as Create Purchase Order.
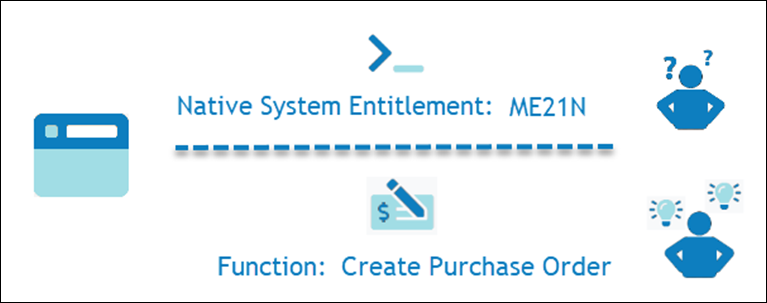 Figure 1. Translating a native system entitlement (ME21N) into a business-friendly Function.
Figure 1. Translating a native system entitlement (ME21N) into a business-friendly Function.
By translating technical entitlements into intuitive business terms, Functions help ensure access rights are meaningful to both technical and non-technical stakeholders, improving governance and risk review processes.
Types of Functions
EmpowerID distinguishes between two levels of Functions:
Global Functions
Global Functions are system-agnostic and represent actions that apply across multiple systems. For instance, a Global Function such as Create Group might apply to systems like Azure AD, Salesforce, and SAP.
 Figure 2. Example of a Global Function applied across multiple systems.
Figure 2. Example of a Global Function applied across multiple systems.
Local Functions
Local Functions are specific to a system, business unit, or geographic location. These Functions provide a more granular view, such as Create Purchase Order in SAP Production or Create Groups in Austria. Local Functions are always linked to a parent Global Function.
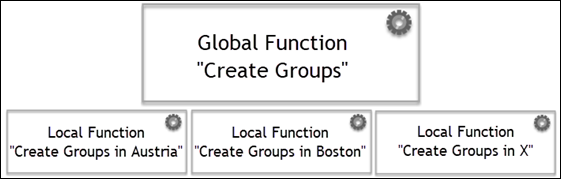 Figure 3. Local Functions derived from a single Global Function.
Figure 3. Local Functions derived from a single Global Function.
Function Mapping
Function mapping establishes the relationship between Functions and the technical entitlements (rights and roles) in your systems. This is done at both the Global and Local Function levels.
Global Function Mapping
When defining a Global Function, administrators can add mapping rules that associate the Function with:
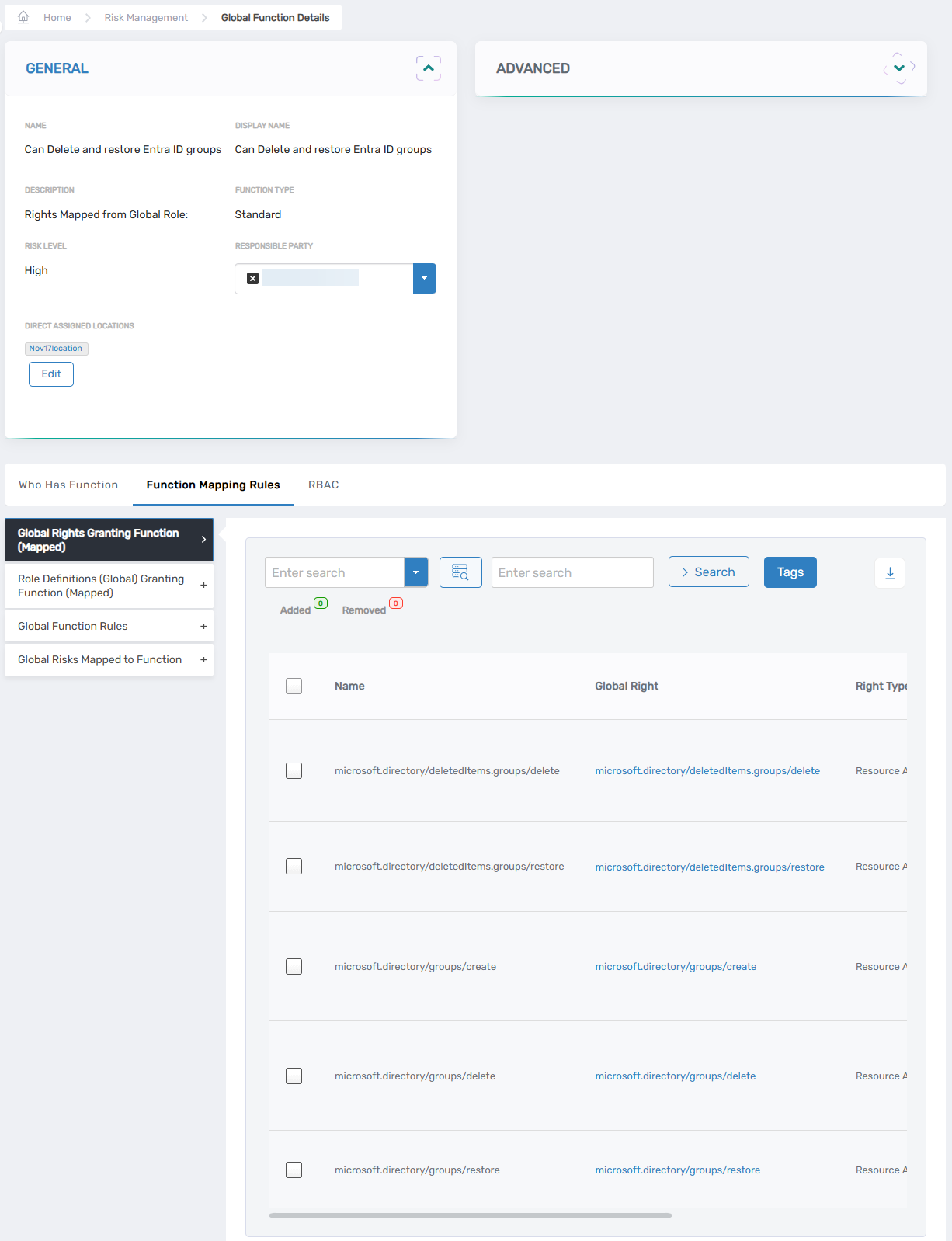 Figure 4. Global Function Mapping rules in EmpowerID, linking Functions to entitlements.
Figure 4. Global Function Mapping rules in EmpowerID, linking Functions to entitlements.
- Global Rights Granting Function – Specifies any global rights linked to the Function
- Global Roles Granting Function – Specifies any global roles linked to the Function
- Derived Local Functions – Identifies Local Functions that stem from this Global Function
Local Function Mapping
Once Local Functions are created from Global Functions, administrators can map them to more specific entitlements:
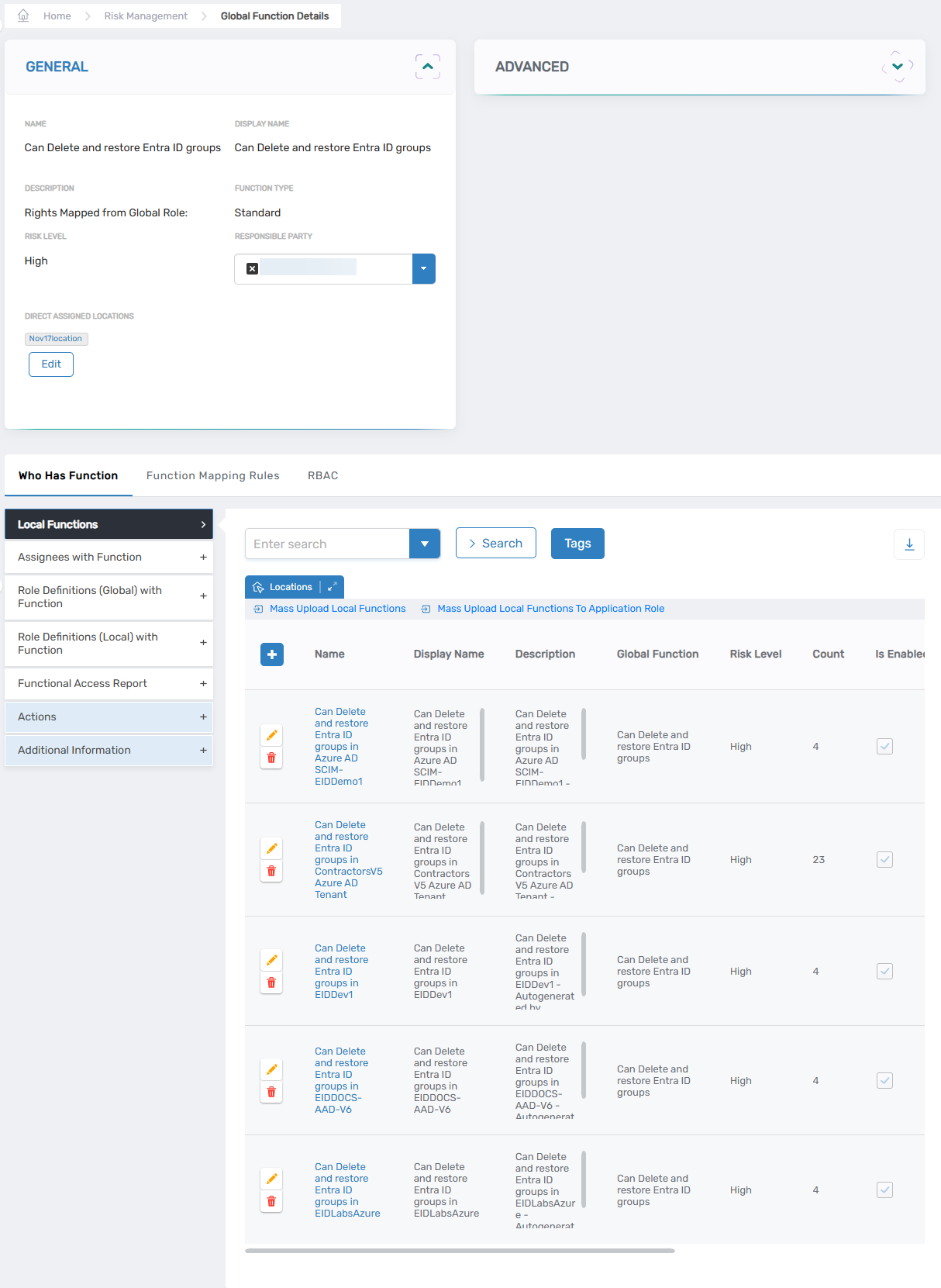 Figure 5. Local Function mappings.
Figure 5. Local Function mappings.
- Local Rights Granting Function – Maps local system rights to the Function
- Local Roles Granting Function – Maps local roles to the Function
- Assignees Granting Local Function – Specifies which identities are flagged as having the Function. These can include:
- Business Role and Location
- Groups
- Management Roles
- Management Role Definitions
- Specific Persons
- Query-Based Collections
Only rights and roles already mapped to the parent Global Function can be assigned at the local level.
Risk Management with Functions
Each Function in EmpowerID can be assigned a risk level based on the potential impact of the activity it represents. These risk scores help the Risk Engine assess the overall access-related risk for each user.
Risk Levels:
| Risk Level | Score |
|---|---|
| Low | 0 |
| Medium | 30 |
| High | 60 |
| Critical | 80 |
| Very Critical | 100 |
The Risk Engine aggregates scores for all Functions assigned to a user, whether directly or via role or group membership, and calculates a total risk score. This enables administrators to identify and prioritize users with elevated access risk.
Summary
Functions in EmpowerID provide a structured way to align technical entitlements with business activities. By defining Global and Local Functions, mapping them to entitlements, and assigning risk scores, organizations can gain better visibility into user access and implement more effective governance and risk controls.