About Risk Management
Risk management in today's business environment involves systematically identifying, assessing, and controlling threats to a company's IT resources. The ultimate goal is to ensure businesses operate smoothly and maintain compliant access to their systems.
What is Compliant Access?
Compliant access minimizes potential risks associated with granting access to company resources, such as computer systems, applications, and software. It ensures that access is aligned with an employee’s role and adheres to regulatory rules, industry standards, and company policies. This approach defines what is considered acceptable, risky, or non-compliant regarding access rights.
Challenges with Traditional Risk Management
Traditionally, enterprises face significant challenges in managing risks spread across multiple cloud and on-premise systems. This complexity is often exacerbated by overlapping system access. To effectively manage these risks, companies must deeply understand the permissions model for every application they use to prevent excessive access that increases risk. EmpowerID addresses this complexity through its comprehensive Identity Governance and Administration (IGA) connector library, integrating diverse permissions models and enhancing control over system access.
EmpowerID’s Approach to Bridging Gaps
Despite the technical prowess of many IAM solutions, they often fail to link system entitlements to business processes in a user-friendly manner. For example, the entitlement to create a purchase order in an SAP system is represented by the TCode ME21N. While clear to technical specialists, this may not be intuitive for business users. EmpowerID addresses this gap by translating complex entitlements into easily understandable terms, thus enhancing transparency and control.
EmpowerID Risk Management Strategy
EmpowerID recognizes that each organization has unique process definitions and policy needs. It tailors risk management solutions to accommodate these characteristics, simplifying complex terminologies into plain language for business users while preserving necessary technical details for IT professionals.
Integrating Business Models
Understanding that businesses operate through continuous processes to deliver products or services, EmpowerID breaks down these processes into manageable "business-defined activities." These activities are mapped to specific rights and roles within the system, known as "function mapping," enhancing visibility into potential risk areas.
Function Mapping and Risk Management
EmpowerID leverages function mapping as the critical bridge between technical entitlements and business processes, translating complex access management concepts into understandable, business-friendly terms. All organizational activities are decomposed into specific business processes consisting of various functions requiring technical entitlements.
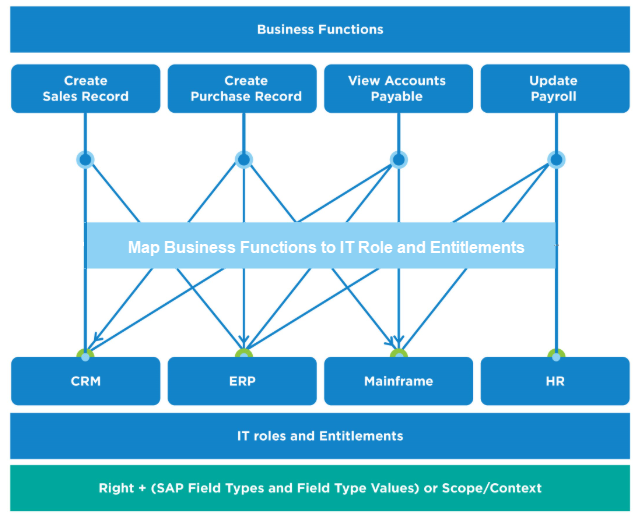
Functions are categorized into:
- Global Functions: Actions standardized across multiple systems, linked to global risks.
- Local Functions: Specific to individual systems or locations, linked to local risks.
Defining and Understanding Risks
Effective risk management involves defining which functions carry significant risks and specifying combinations of functions potentially leading to fraud or adverse outcomes. Risks defined at the function level enhance clarity and visibility into activities requiring monitoring.
Risk Rules and Segregation of Duties (SOD)
Risk rules in EmpowerID specify memberships (Management Roles, groups, Business Roles and Locations, etc.) that cause risk violations. Risk-to-Function mappings detail relationships between functions constituting a risk. Risk rules highlight calculated outcomes identifying exact memberships causing risk violations.
Preventative and Detective Controls
Risk management incorporates:
- Preventative Controls: Real-time visibility during access requests.
- Detective Controls: Scheduled evaluations of access and attribute changes.
Risk Owner Responsibilities
Potential violations identified through controls are escalated to risk owners for evaluation, approval, or rejection based on risk implications and mitigation strategies.
Next Steps
To effectively implement EmpowerID’s risk management capabilities, review the following sections within this guide:
- Risk Management Tasks for task-based implementation guidance, including configuring risk policies and managing risk violations.
- Business Function Intelligibility for detailed information on function mapping and its role in defining compliant and non-compliant access.