Recertification Architecture and Process Flow
Recertification in EmpowerID ensures user access rights are regularly validated to align with roles and compliance standards. The recertification process is structured around clearly defined stages, each designed to effectively maintain organizational security and compliance. The following diagram visually represents the entire process, showing the interaction between policy creation, audit execution, decision-making, and fulfillment.
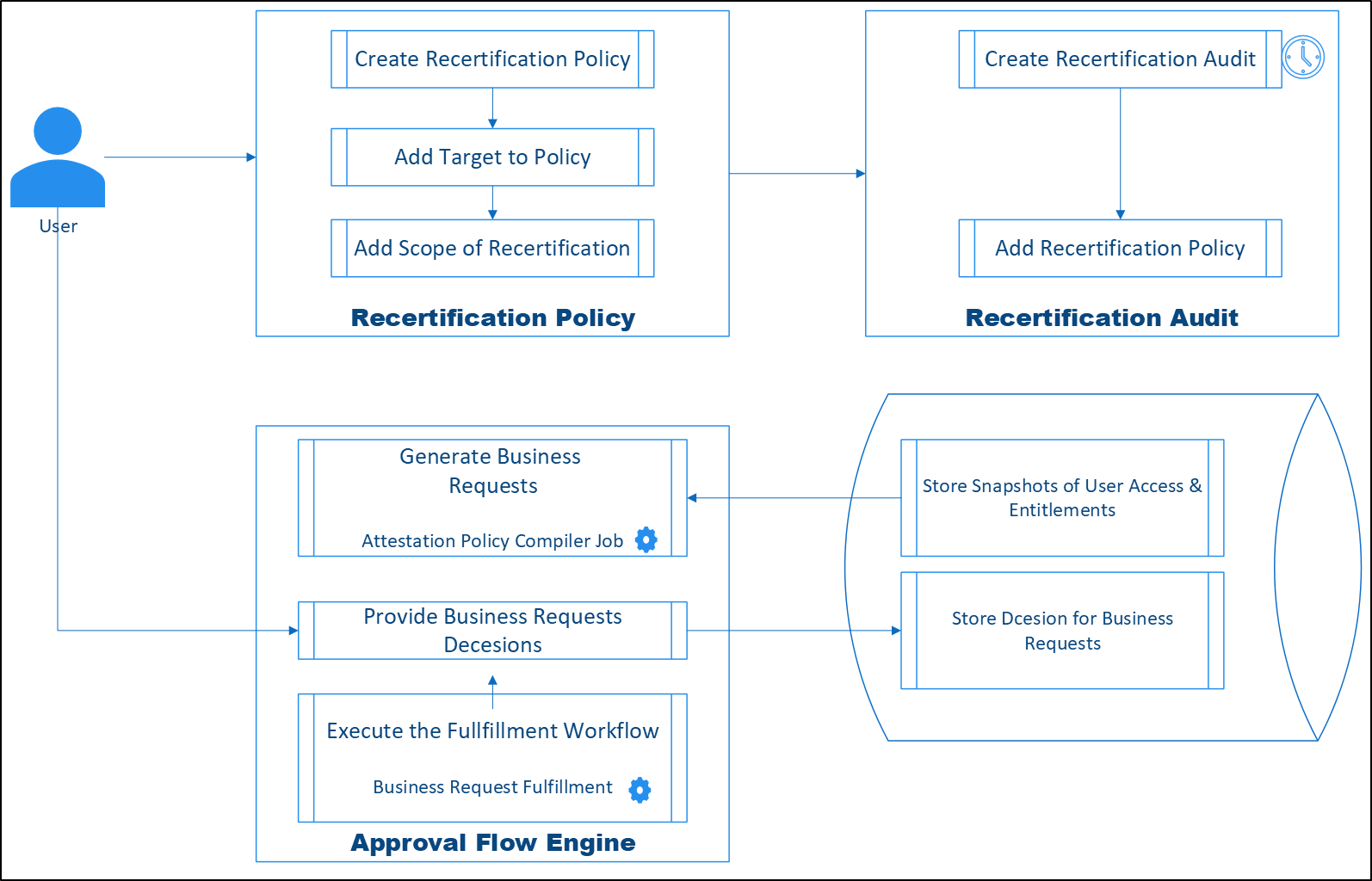
The diagram above illustrates how each step in the recertification workflow connects logically, creating a streamlined process that continuously maintains accurate access controls.
Establishing the Recertification Policy
The process begins by clearly defining the recertification policy. This foundational step is crucial as it specifies exactly what, who, and how the access review should be performed.
Initially, administrators create a Recertification Policy, specifying its type—such as group memberships or account validity—and enable it for auditing purposes. Subsequently, they determine the policy’s targets, clearly defining the users, groups, or locations subject to recertification. Lastly, they add an Item Type Scope (Data), outlining precisely what data should be collected and reviewed, such as group memberships or specific user permissions.
Initiating Recertification Audits
With clearly defined policies in place, administrators create recertification audits to operationalize these policies. These audits are typically scheduled based on compliance requirements or organizational preferences.
Each audit is explicitly linked to one or multiple recertification policies. This linkage ensures comprehensive coverage across different resources and user roles, enabling thorough and consistent recertification efforts throughout the organization.
Conducting the Audit
When an audit runs, the EmpowerID recertification engine systematically gathers data to create snapshots representing the current access state of targeted resources. These snapshots become the basis for review tasks, known as Business Request Items, which are then automatically assigned to designated reviewers or auditors.
During the review phase, approvers assess each item to determine whether the current access should continue (certified) or be revoked. Their decisions directly influence subsequent actions and workflows.
Executing Decisions and Fulfillment
Once reviewers make their decisions, EmpowerID immediately triggers the corresponding workflows to implement these decisions. The fulfillment workflows ensure that certified access remains intact, while rejected access is promptly revoked or adjusted.
Several automated jobs and workflows actively support and streamline this stage:
Key Jobs Supporting the Audit Execution
- Attestation Policy Compiler: Collects and compiles data necessary to create and distribute Business Request Items.
- Business Request Approvers Refresher: Ensures approvers remain updated about pending tasks and any escalations.
- Business Request Fulfillment Job: Carries out the actions (maintaining or revoking access) decided by auditors.
- Business Request Notification Inbox Claim Job: Manages and sends notification emails regarding pending review tasks.
- Business Request Notification Inbox Drop Processor: Processes notification events generated during the recertification.
- Permanent Workflow Job: Maintains continuous operation of recertification-related workflows.
- Notification Report Subscription Compiler: Consolidates and sends daily summary notifications to users, simplifying task management.
Permanent Workflows Ensuring Continuous Compliance
- Create Scheduled Certification Audit: Automatically initiates scheduled audits, ensuring consistent recertification timing.
- Close Revoke Recertification Unreview Task After Audit Due Date: Closes tasks left unreviewed past their due date using predefined policy settings.
This structured, automated approach ensures ongoing access integrity, compliance, and security.